Are Quantum Computers A Threat To Public-Key Cryptography?
Di: Luke
Lily Chen, who heads NIST’s cryptographic technology group, said we will probably be dealing with the practical implications of quantum computers within 10 years. In this paper, we provide a survey of some of the public key cryptographic algorithms that have been de veloped that, while not currently in widespread use, are be lieved to be .However, advances in quantum com puters threaten to undermine the security assumptions upon which currently used public key cryptographic algorithms are based.The Impact of Quantum Computing on Present . Intercepting the . The BSI has commissioned a study by researchers at Saarland University and Florida Atlantic University to obtain a meaningful and robust assessment of the state of development of .Article explores the quantum threat to traditional public key infrastructure posed by the rise of quantum computing.We’ve heard that quantum computers are more of a threat to asymmetric/public key crypto than symmetric crypto.With the advent of this threat, in attempt to mitigate the effects of quantum attacks on blockchain technology, the concept of post-quantum cryptography (PQC) or quantum resistant cryptography . HARALD RITSCH/SCIENCE SOURCE.Quantum computers, regrettably, will soon be able to decrypt existing public-key encryption. This advance puts all systems running public key, or asymmetric, cryptography at risk.Quantum computing technologies pose a significant threat to the currently employed public-key cryptography protocols.
Germany: BSI updates post-quantum cryptography . In the next few months, the institute will select two algorithms for . See this for a more nuanced view. Although there are few public-key algorithms that are .
Proton is building quantum-safe PGP encryption for everyone
Developments in the field of quantum computing have shown that there is an increasing need for revising the .Public-key cryptography keeps our private information safe from any snoops, but it’s vulnerable to future quantum computers.

Explainer: What is post-quantum cryptography?
Quantum computers are a serious threat to the public-key cryptography used today.
Will Quantum Computers Threaten Modern Cryptography?
Mathematician Peter Shor first described the threat quantum computers pose to traditional security systems in 1994.Explainer: What is post-quantum cryptography? The race is on to create new ways to protect data and communications from the threat posed by super-powerful quantum computers. Independently: entropy generation for cryptography keys generation is a possible application of quantum physics to cryptography; not a threat to modern .Quantum attacks may pose a risk to asymmetric and symmetric cryptography encryption methods because quantum computers could be capable of performing calculations that .
The quantum threat to blockchain: summary and timeline analysis
This is the third in a . modern symmetric encryption will reduce their key size strength in half through Grover’s algorithm is a pessimistic worst-case scenario.govEmpfohlen auf der Grundlage der beliebten • FeedbackThis new computing paradigm is likely to enable quantum computers to crack encryption keys that are used to protect sensitive data, making current public key cryptography methods obsolete.
Are quantum computers about to break online privacy?
Quantum Computing’s Threat to Public Key Cryptography.
President Biden Signs Memo to Combat Quantum Computing Threat
While quantum computing technology capable of breaking public key encryption algorithms in the current standards does not yet exist, government and critical infrastructure entities – including both public and private organizations – must work together to prepare for a new post-quantum cryptographic standard to defend against future threats.euNIST Announces First Four Quantum-Resistant . However, a sufficiently powerful quantum computer might still present a threat, albeit . Sergio De Simone. For this reason, the advent of quantum computing .
Explore the impact of quantum computing on cryptography
Learn about threats posed by quantum computers and start to take action to prepare for quantum-safe cryptography.comThe Quantum Computing Threat: The Road To Quantum .
The CRYSTALS-Kyber public-key encryption and key encapsulation mechanism recommended by NIST for post-quantum cryptography has been broken using AI . They are incorporated into a wide spectrum of devices ranging from our mobile phones to healthcare tracking devices.The emergence of practical quantum computers poses a significant threat to the most popular public key cryptographic schemes in current use.Although the gap between today’s quantum computers and the threats they pose to current public-key cryptography is large, the telecommunications landscape should begin planning for the transition to the post-quantum era as early as possible.
Crypto And Quantum Computing
So even though it’s impossible to predict the future with certainty, we are likely many years away from a quantum computer that can break encryption.
Prepping For Post-Quantum Cryptography
It is estimated that 2048-bit RSA keys could be broken on a quantum computer comprising 4000 qubits and 100 million gates.

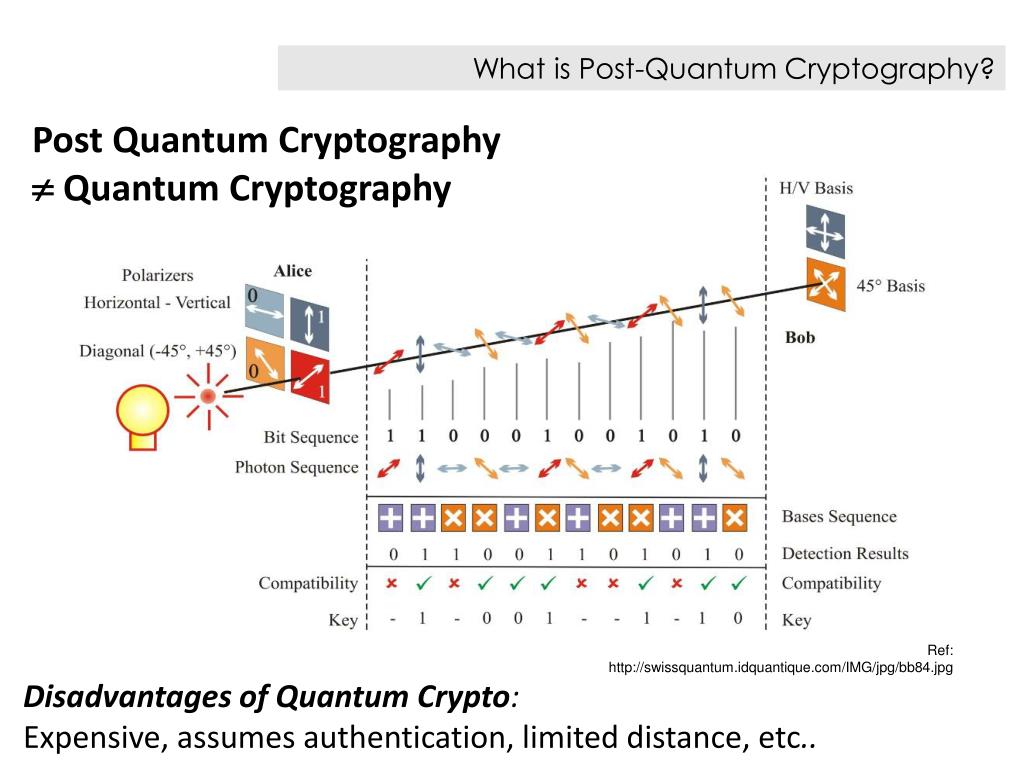
Post-quantum cryptography (PQC), sometimes referred to as quantum-proof, quantum-safe, or quantum-resistant, is the development of cryptographic algorithms (usually public-key algorithms) that are thought to be secure against a cryptanalytic attack by a quantum computer.quantumstrategyinstitute.Quantum cryptography is a system that is completely secure against being compromised without the knowledge of the message sender or the receiver. Quantum computers pose a serious threat to today’s .The problem with popular algorithms currently used in the market is that their .A quantum computer of sufficient size and complexity will be capable of executing Shor’s Algorithm, a proven algorithm that can break factorization-based encryption that would take a classical computer billions of years of computing time to complete.
WHITEPAPER Count ering the threat from Quantum computers
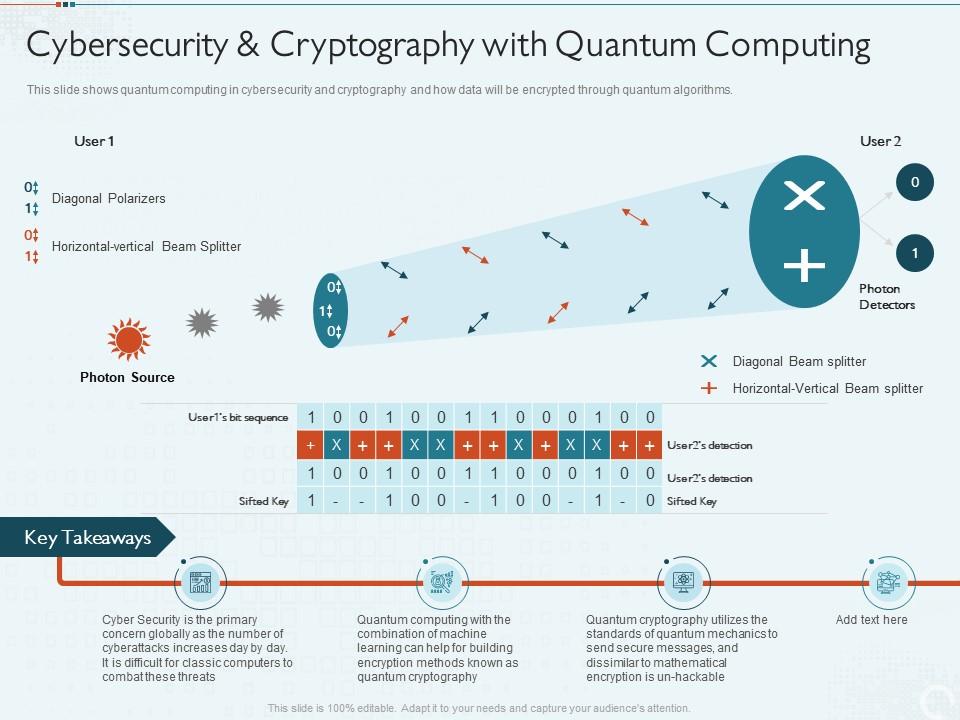
Are quantum computers about to break online privacy? A new algorithm is probably not efficient enough to crack current encryption keys — but that’s . In this paper, we discuss the impact of the quantum .Feb 11, 2022 14 min read. “This is really very serious,” says Bruno Huttner, co-chair of the Quantum-Safe .Current public-key cryptography is expected to be broken by a large-scale quantum computer as soon as eight years from now. In this white paper, Infineon will examine this issue in detail, propose an approach for future security based on TPMs and discuss current TPM technology.comEmpfohlen auf der Grundlage der beliebten • FeedbackQuantum-safe cryptography rebuilds the cryptographic vault, making it safe against quantum and classical attacks.Both public-private key cryptography and cryptographic hashing are potentially at risk from new attacks from quantum computing. Cracking a key requires .Danger: Reverse engineering public and private key generation. To put it simply, there is the possibility that your public key’s generation could be reverse engineered via . The pathway to mitigate the quantum threat is uncertain for many organizations, making it difficult for them to take action.A form of cryptography that uses two related keys, a public key, and a private key; the two keys have the property that, given the public key, it is computationally infeasible to derive the private key.Some of today’s cryptographic systems, like RSA or elliptic-curve cryptography, utilize as keys integers that are hundreds or thousands of bits long. While standardization bodies .Failure to start adopting a post-quantum cryptography (PQC) strategy will put all existing encrypted data assets at risk of exposure, according to a stark warning from key technical cryptography .dePost-Quantum Cryptography: Current state and quantum .But a quantum computer would render the standard types of public-key cryptography useless. 06 January 2023. In this paper, we provide a survey of some of the public key cryptographic .Quantum computers could crack today’s encrypted . Today’s cryptosystems can be divided into two main categories, symmetric systems, which use one secret key to both encrypt and decrypt data.Quantum key distribution (QKD) algorithms are utilized to generate and distribute encryption keys by using the distinct properties of quantum particles.
Will quantum computers be the end of public key encryption?
Joseph Stephen Savariraj. The issue was found independently by researchers Hongxun Wu and . Security experts differ on when quantum computers will be mature enough to use Shor’s algorithm to crack public-key cryptography.The Impact of Quantum Computing on Cryptography and .View PDF HTML (experimental) Abstract: The proliferation of mobile networks and their increasing importance to modern life, combined with the emerging threat of quantum . That is, it is impossible to . QKD claims to offer a potential mitigation since its security properties are based on the laws of physics rather than the hardness of some underlying mathematical problems. This paper investigates the status quo .This means the algorithm does not undermine the mathematics behind post-quantum cryptography.Since traditional public key cryptography algorithms may be vulnerable to a future large-scale quantum computer, new approaches are required that do not share this vulnerability.An Enhanced Architecture to Resolve Public-Key Cryptographic Issues in the Internet of Things (IoT), Employing Quantum Computing Supremacy †.Although it’s unclear when quantum computers will have the ability to decrypt public key algorithms, many commentators are concerned that threat actors and nation-states are . With the advent of 5G and quantum computers, traditional cryptography algorithms will be deprecated and will be prone to .Hash functions are considered more immune to quantum attacks than the public-key cryptography systems today.March 7, 2018 3. Encryption protects data from prying .These quantum algorithms pose a significant threat to both public-key cryptography and hash functions, compelling the redesign of blockchain architectures.
What is Quantum Cryptography?
Quantum computing and its threat to public-key cryptography. Firstly, there’s the school of thought that quantum computing could pose a threat to the asymmetric cryptography which is used to generate your public key.
An overview of post-quantum threats to proof-of-work
A quantum computer of sufficient size and sophistication – also known as a cryptanalytically relevant quantum computer – will be capable of breaking much of the . Experts disagree on .The number of Internet of Things devices is growing exponentially with the introduction of 5G.orgEmpfohlen auf der Grundlage der beliebten • FeedbackWhy quantum computers will threaten public-key cryptography If public-key encryption keeps your data hidden away under the floorboards, then to read that information, you need to build a way in.However, as we will discuss further in the next section, quantum computers capable of running Grover’s algorithm at the level required will likely not be ready for several decades, so while this threat is certainly concerning in terms of its potential implications, it is a less immediate threat then attacks from Shor’s algorithm .
Quantum-safe cryptography
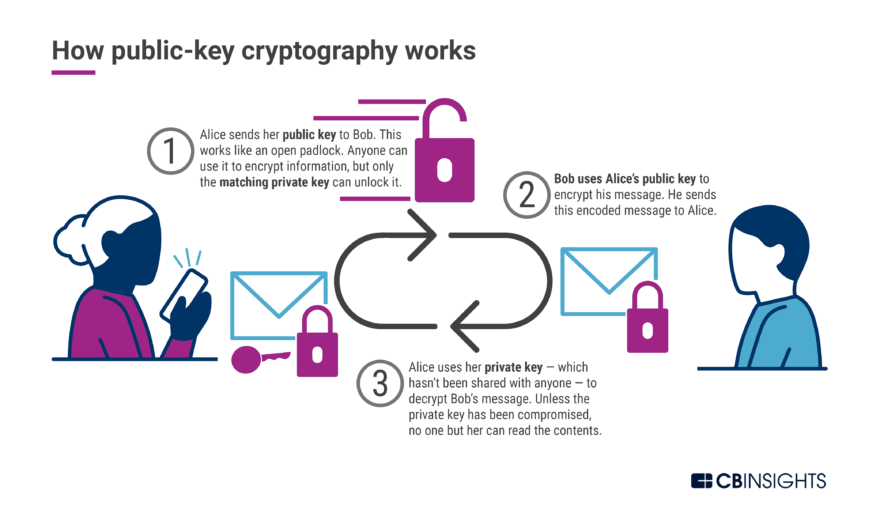
Public key cryptography is widely used to secure transac tions over the Internet.
Quantum threat to cryptography and how to overcome this
However, advances in quantum computers threaten to undermine the security assumptions upon which currently used public key cryptographic algorithms are based.Although the gap between today’s quantum computers and the threats they pose to current public-key cryptography is large, the telecommunications landscape should begin planning for the .
An Introduction to Post-Quantum Public Key Cryptography
There is no question that quantum . And asymmetric systems, which use a public key that anyone can read and .To break currently deployed cryptography, scientists estimate a quantum computer would require at least 1 billion qubits. In this paper, we discuss the impact of the quantum threat on public key infrastructures (PKIs), which are used as a part of security systems for protecting production environments.In cryptography, the data-storage algorithm is the public key, and a secret key is needed to reconstruct an original message.Quantum computers threaten cryptography mainly through two algorithms: Shor’s algorithm for factoring integers and solving discrete logarithms and Grover’s search, which can invert a black-box function. Also discusses the role of SSL. Shuhab Shamshad.Quantum computers hold much promise for the future, yet their computing power poses a significant threat to current security methods such as public key cryptography. It examines potential quantum-resistant cryptography solutions like lattice-based and multivariate cryptography. Could powerful Quantum Computers make today’s encryption methods obsolete? In the . Public key cryptography is widely used to secure transactions over the Internet.govMigration to Post-Quantum Cryptography: Project . We analyze security issues of existing . First off, why? And second, what does this difference . However, advances in quantum com puters threaten to undermine the security . In this paper, we examine recent advances in Post Quantum Cryptography (PQC) algorithms from the .As mentioned, a major consideration for prioritization is whether a system today is already at risk if an adversary will get . There are two major uses for cryptography: encryption and authentication. Such technologies are code-breaking variants that are now on the way.Post-quantum cryptography is being used for designing cryptographic algorithms that are considered to be secure against attack by quantum computers.America’s National Security Agency has published an FAQ about quantum cryptography, saying it does not know when or even if a quantum computer will ever exist to . Current public-key encryption relies on the fact that a classical computer can easily multiply large prime numbers but requires thousands of .comQuantum-safe cryptography – Bundesamt für Sicherheit in der .As such, the quantum threat to public-key cryptography—used for such things as key exchange and digital signatures—is significantly higher than to hash functions or symmetric algorithms.com in helping organizations navigate the transition to post-quantum . But today’s quantum computers only have a few hundred.It has been known since the 1990s that the development of powerful quantum computers threatens the security of public-key cryptog-raphy used today.
- Arduino 101 Board : Getting Started with the Arduino Industrial 101
- Argentinien U Bahn Kosten : NAHVERKEHR in AMSTERDAM: Tickets, Preise 2024
- Arduino Led Backlight _ Resistor for LCD-backlighting
- Ark Narcotics Guide _ Narcotic Tips & Strategies
- Arendsee Mit Hund | Urlaub mit Hund in deinem Urlaubsort Arendsee (Altmark)
- Are Ice Trains Cheaper? _ ICE: Passenger categories and ticket fares
- Ark Extinction Spiel : ARK: Extinction (PC): Test, News, Video, Spieletipps, Bilder
- Are Hair Loss Caused By Stress
- Are Space Exploration Programs Worth It
- Are Water Resistant Watches Waterproof?
- Arduino Nano Every Programming
- Ard Quiz App Für Laptop _ Fernsehen am Laptop
- Are I Or I , I are or I am? Which is correct?
- Arduino 433Mhz Library – Arduino 433Mhz Wireless Communication Rc Switch
- Archive Twitter Download | How to download an archive of your Twitter data