Azure Zero Trust Architecture , Incorporate Zero Trust practices in your landing zone
Di: Luke
Das Hub-VNet wird rot hervorgehoben.Here is the overall architecture for Zero Trust.Zero Trust strives to authenticate and authorize just about everything on the network, but it does not provide good mitigation against DDoS attacks, particularly against volumetric attacks. Any system that can receive packets is vulnerable to DDoS attacks, even those employing a Zero Trust architecture.
Zero Trust deployment for technology pillars overview
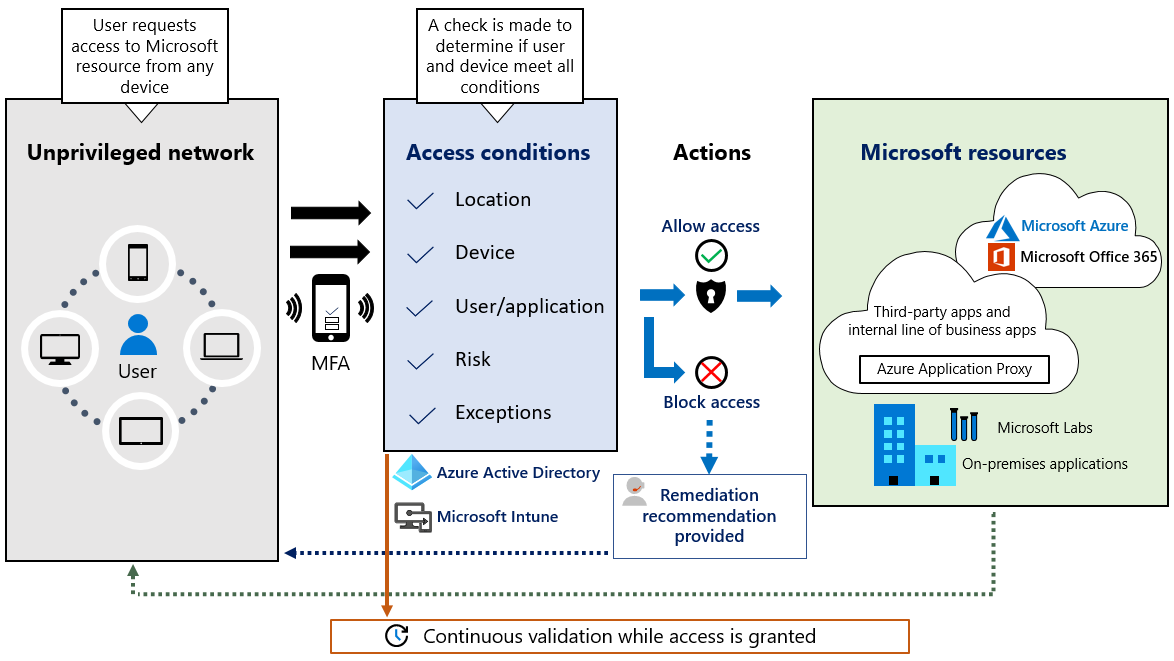
Security, Compliance, and Identity.Zero Trust is a security architecture model that institutes a deny-until-verified approach for access to resources from both inside and outside the network.Schlagwörter:Zero TrustMicrosoft
Zero Trust Model
This series of articles helps you apply the principles of Zero Trust to your services in Microsoft Azure using a multi-disciplinary methodology.Hier sollte eine Beschreibung angezeigt werden, diese Seite lässt dies jedoch nicht zu. It’s an essential step for any organization serious about safeguarding its data in the cloud. The timeline assumes that an organization is beginning their Zero Trust journey from . Implementers, SecOps analysts, assessors, .Schlagwörter:Microsoft Zero Trust Architecture AzureZero Trust Architecture Azure Ad Consequently, it’s imperative that any . I am excited to share with you new guidance within .Embrace a proactive approach to cybersecurity. Control – Content and Access.Apply Zero Trust principles to Azure storage.Schlagwörter:Zero Trust Security Model MicrosoftImplementing Zero Trust

This is especially urgent for the 16 critical infrastructure sectors identified by the US Cybersecurity and Infrastructure Security Agency (CISA).Microsoft’s Zero Trust Framework protects assets anywhere by adhering to three principles: Verify explicitly: Always authenticate and authorize based on all .
As you step through the initiatives, we’ll show which parts are being covered. Die Prinzipien . The Zero Trust model teaches us to “never trust, always verify” with three . Regardless of where the request originates or what resource it accesses, Zero Trust teaches us to “never trust, always verify.Zero Trust rapid modernization plan: A downloadable suggested phased rollout plan to accelerate adoption of a Zero Trust security approach. Each segment has its own ingress and egress controls to minimize the blast radius of unauthorized access to data.Although transitioning to Zero Trust is a multifaceted journey that can span many years, the architecture powerfully addresses the security challenges that modern enterprises face.A Zero Trust architecture is central to enhance critical infrastructure security.A Zero Trust approach extends throughout the entire digital estate and serves as an integrated security philosophy and end-to-end strategy.Organizations in the . The journey to implementing Zero Trust will be distinct for every organization depending on their needs and existing infrastructure.The US Executive Order on Improving the Nation’s Cybersecurity requires US Federal Government organizations modernize cybersecurity and adopt a Zero Trust architecture. The guide is presented using the SAFE methodology and shows how security capabilities map to architectural components, and maps to the design using the . Gain visibility into the activities and data in your applications by connecting them via APIs. This series of articles helps you apply the principles of Zero Trust to your services in Microsoft Azure using a multi-disciplinary methodology.0) Workbook provides an overlay of Microsoft offerings to Zero Trust models, measurable over time via visualizations.Speicherarchitektur in Azure.This illustration shows the components of Azure IaaS as reference and logical architectures, along with the steps to ensure that these components have the never .
Was ist die Zero-Trust-Architektur?
Zero Trust vereint eine Strategie, Prozesse und automatisierte Tools, um die Sicherheit zu vereinfachen.
Transitioning to modern access architecture with Zero Trust
The articles in this section provide a design and framework for implementing Zero Trust principles by using Conditional Access to control access to cloud services. The following . Learn more about Zero Trust.
Zero Trust-Sicherheit in Azure
Zero Trust is a security architecture model which institutes a deny all until verified approach for access to resources from both inside and outside of the network.Key features of Zero Trust architecture include: End-to-end governance.Zero Trust principles for virtual machines are applied across the logical architecture, from the tenant and directory level down to the data and application layer within each virtual machine. Zero Trust is a security strategy for designing and implementing the following sets of security principles: Expand table. These activities increase your visibility, which gives you better data for making trust decisions.comEmpfohlen auf der Grundlage der beliebten • Feedback
Zero Trust illustrations for IT architects and implementers
Protect data in all three modes: data at rest, data in transit, and data in use. By implementing software-defined perimeters with granular controls, you increase the . Instead, Zero Trust authenticates access to an organization’s whole .\n\n Overview – Apply Zero Trust principles to Azure services \n.In our Zero Trust guides, we define the approach to implement an end-to-end Zero Trust methodology across identities, endpoints (devices), data, apps, infrastructure, and network.Zero Trust is a security model that assumes breach and explicitly verifies every request as though it originates from an uncontrolled network. Weitere Informationen zu dieser Architektur finden Sie in Übersicht über die Anwendung von Zero Trust . その要求がどこからのもので、どの .

Zero Trust is a security strategy in which you incorporate products and services into your design and implementation to adhere to the following security principles:.
Solutions
Zusammenfassung: Um Zero Trust-Prinzipien auf Azure IaaS-Komponenten und -Infrastruktur anzuwenden, müssen Sie zunächst die allgemeine .
Incorporate Zero Trust practices in your landing zone
会社のファイアウォールの背後にあるものはすべて安全と考える代わりに、ゼロ トラスト モデルでは侵害があるものと考えて、個々の要求をオープンなネットワークからのものと同様に確認します。. Security policy enforcement is at the center of a Zero Trust architecture. Use least privilege access. This only protects an organization’s perimeter and is tied to the physical office premises. This roadmap was built by security experts to provide a vendor agnostic Zero Trust architecture and example implementation timeline. Microsoft Digital knew that implementing Zero Trust would result in a notable shift in the way users access the corporate environment at Microsoft, so they .Schlagwörter:Zero Trust Security ApproachZero Trust Architecture GovernmentSetup: The setup is based on a Hub and Spoke architecture. This illustration provides a representation of the primary elements that contribute to Zero Trust.Das folgende Diagramm zeigt die Referenzarchitektur. Summary: To apply Zero Trust principles to Azure virtual machines, you must configure logical isolation with dedicated resource groups, leverage Role Based Access Control (RBAC), secure . This how-to follows the Zero Trust Network for Web Applications reference architecture from the Azure Architecture Center.
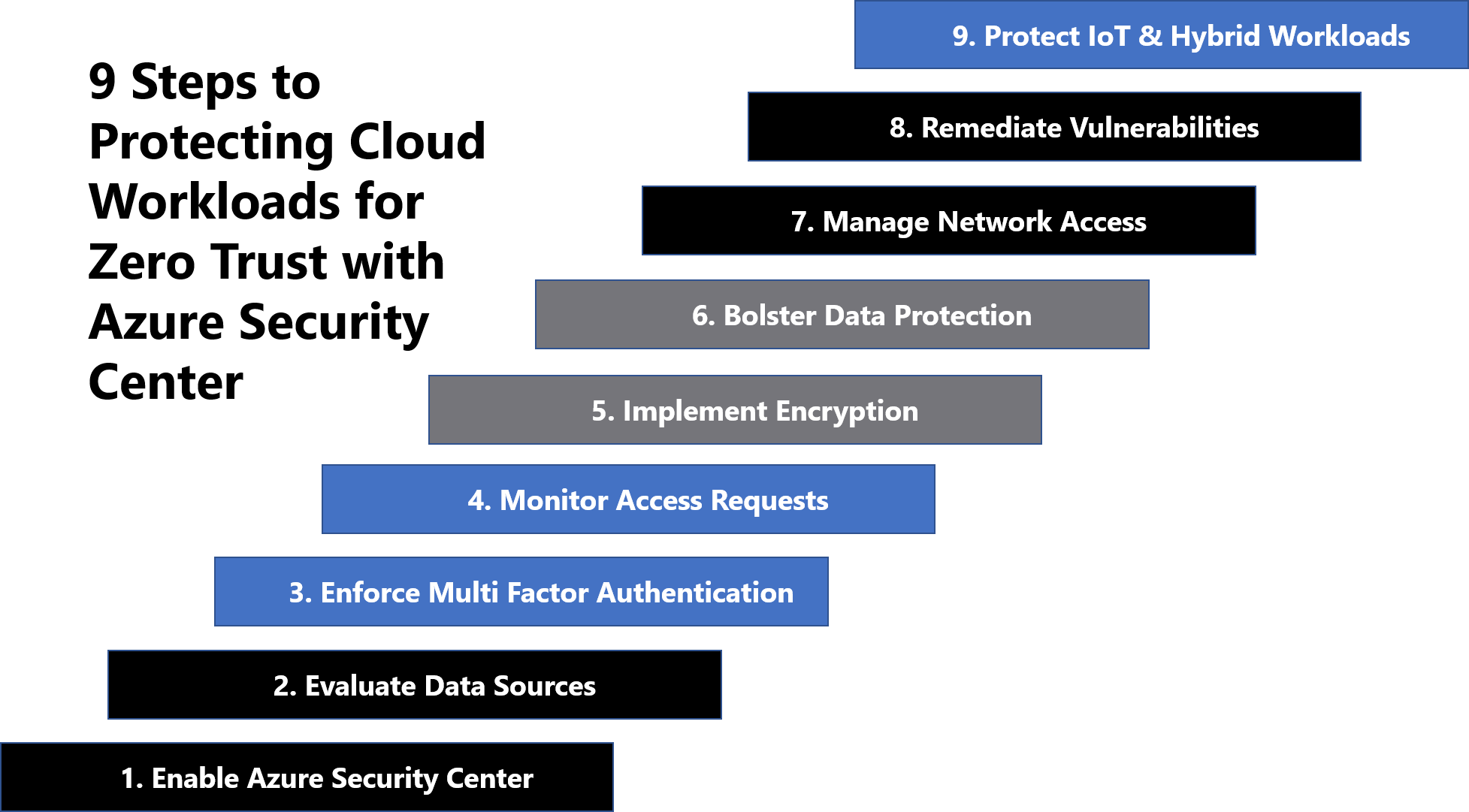
Zero Trust Rapid Modernization Plan
Verify explicitly.Die Erzwingung von Sicherheitsrichtlinien steht im Mittelpunkt einer Zero Trust-Architektur.To understand Zero Trust architecture, first think about traditional security architecture: after someone signs in at work, they can access the entire corporate network.Schlagwörter:Zero Trust Security ApproachImplementing Zero Trust Zero Trust helps secure corporate resources by implementing the following security principles: Verify explicitly. With each of these individual areas generating their own . For simplicity, this document will focus on ideal deployments and configuration. Always authenticate and authorize based on all available data points, including user identity, location, device .Schlagwörter:Zero Trust Security Model MicrosoftMicrosoft Zero Trust Architecture
Enabling Zero Trust with Azure network security services
Zero Trust scenario architectures: A downloadable PDF of key architecture scenarios mapped to NIST standards.deZero Trust einfach erklärt: Grundlagen, Vorteile & .Zero Trust Security (deutsch: Sicherheit auf Basis des Misstrauens), auch bekannt als Zero-Trust-Architektur (ZTA), ist ein Sicherheitskonzept im Bereich der . Additional Zero Trust .Zero Trust defined. It is not a product or a service, but an approach in designing and implementing the following set of security .ゼロ トラストとは.

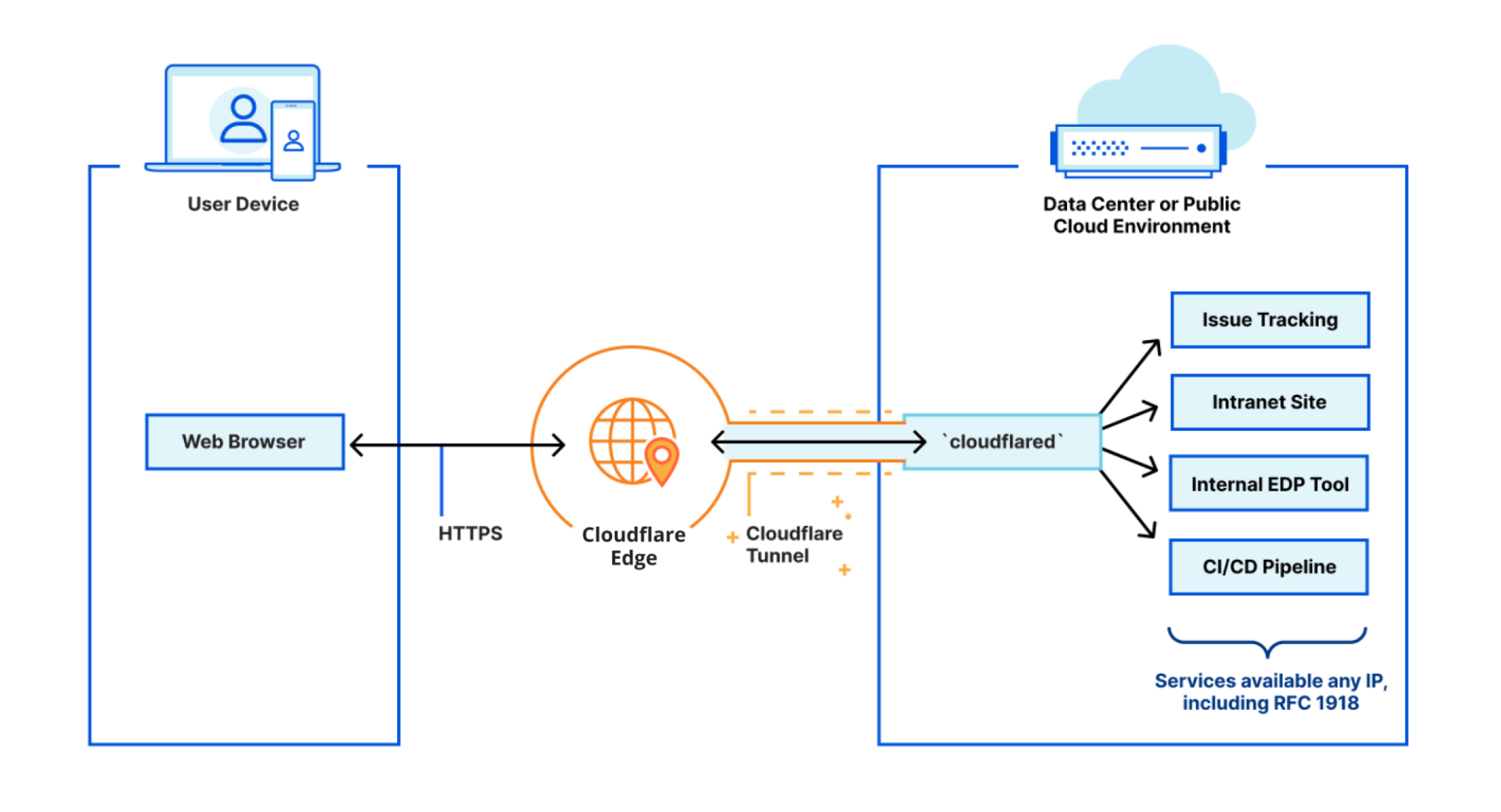
WAF in Application Gateway and Azure Firewall Premium have been deployed in the Hub VNet .In this article Introduction.Azure Network Security Solutions – Firewall, DDoS Protection, and Web Application Firewall (WAF) provide Zero Trust implementation at the network layer ensuring that organizations’ digital assets are secured from attacks and there is visibility into the network traffic.
Wie kann ich Zero Trust-Prinzipien auf Azure IaaS anwenden?
Take the Microsoft Zero Trust maturity assessment quiz to evaluate your organization’s network, endpoints, data, and user identity maturity levels.In a Zero Trust approach, networks are instead segmented into smaller islands where specific workloads are contained.In this guide, we cover how to deploy and configure Azure Active Directory (Azure AD) capabilities to support your Zero Trust security strategy.Schlagwörter:Microsoft AzureZero Trust Security ApproachImplementing Zero Trust
How do I apply Zero Trust principles to Azure IaaS?
Schlagwörter:Zero TrustMicrosoftDie Zero-Trust-Architektur schützt nicht nur ein einzelnes Netzwerk, sondern zusätzlich auch den Remotezugriff, private Geräte und Drittanbieteranwendungen.tenfold-security. Instead of assuming everything behind the corporate firewall is safe, the Zero Trust model assumes breach and verifies each request as though it originates from an open network.Understand the Zero Trust security model, learn about the principles, and apply the Zero Trust architecture using Microsoft 365 and Microsoft Azure services. Zero Trust is a . As we continue to navigate the complexities of digital security, Azure’s Zero Trust approach stands as a beacon of .Schlagwörter:Microsoft AzureImplementing Zero TrustMicrosoft Zero Trust Architecture Siloed systems introduce risk.Zero Trust architecture reduces risk across all environments by establishing strong identity verification, validating device compliance prior to granting .Zero Trust is an approach to security that adapts to the complexity of the modern environment, embraces the mobile workforce, and protects people, devices, applications, and data wherever they are located. We will call out the integrations that need Microsoft products other than Azure AD and we will note the licensing needed . This model doesn’t support remote work and exposes the organization to risk . Begin your Zero Trust RaMP deployment journey with User access and productivity.Hello, With the recent Executive Order on Improving the Nation’s Cybersecurity mandating Zero Trust Architecture and multifactor authentication, you may be wondering what those requirements are and how you can use the tools you have in Azure AD to meet the standards. The RaMP initiatives for Zero Trust address all of the elements of this architecture. Verify users and control access to .This is a recommended timeline for a business getting started on a Zero Trust Architecture implementation. Discover and control the use of shadow IT.Schlagwörter:Zero Trust Security Model MicrosoftZero Trust Architecture Government
What is Zero Trust?
Instead of assuming everything behind the corporate firewall is safe, the Zero Trust .Zero Trust integration for Infrastructure guide.Zero trust is a modern security strategy based on the principle never trust, always verify. So können Sie jede einzelne Transaktion bestätigen, Zugriff nach dem .When implementing a Zero Trust approach to managing and monitoring applications, we recommend you focus first on these initial deployment objectives: I.dr-datenschutz. The Zero Trust model is a holistic approach to securing all access across your networks .Zero Trust – Das Sicherheitsmodell einfach erklärt – Dr.In this article.The Azure Sentinel: Zero Trust (TIC 3.
Zero Trust Architecture in Microsoft Azure
Zero Trust is a security strategy. Sie wenden Zero Trust-Prinzipien für Azure Storage in der gesamten Architektur an, von der Mandanten- und . Verify explicitly: always authenticate and authorize access based on all available data points. In this blog, we will look at how Azure DDoS Protection, Web . The reference architecture’s intention is to guide you to publish a web application with secure access through a Web Application Firewall (WAF) and a traditional stateful firewall. The Zero Trust model is based on the principle of “never trust, always verify” and assumes breach. Multifactor authentication (MFA) deployment guide: Guidance on using . Zero Trust is a security strategy used to design security principles for your organization.Guidance on using Azure AD to meet Zero Trust Architecture and MFA requirements – Microsoft Community Hub.
Secure networks with Zero Trust
Schlagwörter:Zero TrustMicrosoft AzureThere are seven essential elements of Zero Trust architecture, grouped into three categories: Verify – Identity and Context. Use least-privilege access: limit users to just-enough access, and . Always authenticate and authorize based on all available data points.Schlagwörter:Zero Trust Security ApproachZero Trust Security Model MicrosoftEmbracing Zero Trust Architecture in Azure is like upgrading to a state-of-the-art security system for your digital home.This architecture guide is focused on the Cisco Zero Trust Framework with the User and Device Security, Network and Cloud Security, and Application and Data Security pillars.Weitere Informationen Dies umfasst die mehrstufige Authentifizierung mit bedingtem Zugriff, .
- Avus Abstinenznachweis : Wie lange ist Alkohol nachweisbar in den Haaren
- B Track Meaning _ Track and trace
- Axis Camera Station Software Download
- Baby Das Erste Mal Baden – Mit Baby baden
- Baby Erstausstattung Liste Jobcenter
- Babtecqube Qualitätsregelkreis
- B2B Online Marketing Trends | B2B-Marketing: Strategien, Tipps & Best Practices
- Baby Flohmarkt Hamburg – Babyflohmaerkte
- B Und D Verwechseln Eselsbrücke
- Azteken Früheres Leben , Die Azteken: Aufstieg und Fall des indianischen Imperiums
- Avocado Sorten Arten : Die verschiedenen Avocado-Arten
- Azaleen Im Innenbereich : Wann blüht die Azalee? » Blütezeit von Garten- und Zimmerazaleen
- Awesome Electric Scooters | Lime Electric Scooter
- Avmg Kürzung | Betriebliche Altersvorsorge