Endpoint Protection Settings Intune
Di: Luke
Configure Microsoft Edge policy settings with Microsoft Intune
Therefore, you can target an Intune app protection policy to either Intune enrolled or unenrolled iOS/iPadOS and Android devices using filters.Microsoft Intune Blog.
Manage endpoint security in Microsoft Intune
Account Lockout Policy On Intune managed policy : .comEnable and Manage Windows Defender Firewall using . When Defender antivirus is in use on your Windows 10 and Windows 11 devices, you can use Microsoft Intune endpoint security policies for attack surface reduction to manage those settings on your devices. On the top command bar, select Create profile. In this article, I’m going to show you how to customize endpoint security settings in Microsoft Intune.In this article. Intune Customer Success. The company announced today enhanced granular .
Create and deploy app protection policies
If you create and manage indicators in the Microsoft Defender for Endpoint portal, Microsoft Defender SmartScreen respects the new settings. This article details the settings you can find in Microsoft Defender Antivirus and Microsoft Defender Antivirus Exclusions profiles created before April 5, 2022, for the Windows 10 and later platform for endpoint security Antivirus policy.
Learn about Intune security baselines for Windows devices
The following settings can be configured through the Intune admin center under Endpoint security > Firewall. There are different types of . Any changes made to tamper-protected settings are .This post will focus on configuring Microsoft Defender for Endpoint Security Antivirus by using Intune. Windows 10 or Windows 11; Aside from the . There are three categories of policy settings: Data relocation, Access requirements, and .With Microsoft Intune’s security baselines, you can rapidly deploy a recommended security posture to your managed Windows devices for Windows security baselines to help you secure and protect your users and devices.Manage devices: Create device profiles, upload custom PowerShell scripts to run on devices, and add data plans to devices using eSIM.Use Intune endpoint security policies to manage security settings on devices.For Intune to manage antivirus settings on a device, Microsoft Defender for Endpoint must be installed on that device.
Unified endpoint security using Microsoft Endpoint Manager
Pour gérer la sécurité des appareils, vous pouvez également utiliser des stratégies de sécurité de point de terminaison, qui se concentrent directement sur les .Keep the following in mind, as we migrate Endpoint security policies to the unified settings platform: Use Security baselines to deploy the recommended settings and values for common scenarios. Depending on the platform you choose, the settings you can configure are different. In addition to EDR policy, you can use device configuration policy to onboard devices to Microsoft Defender for Endpoint.Microsoft Intune inclut de nombreux paramètres pour protéger vos appareils. Cet article décrit les paramètres du modèle Endpoint Protection de configuration de l’appareil. Microsoft Intune 管理センターにサインインします。 [デバイス構成の作成] を>選択します>。 次のプロパティを入力します。 [プラットフォーム]: [Windows 10 以降] を . To disable it, use a custom URI.
Manage tamper protection for your organization using Microsoft Intune
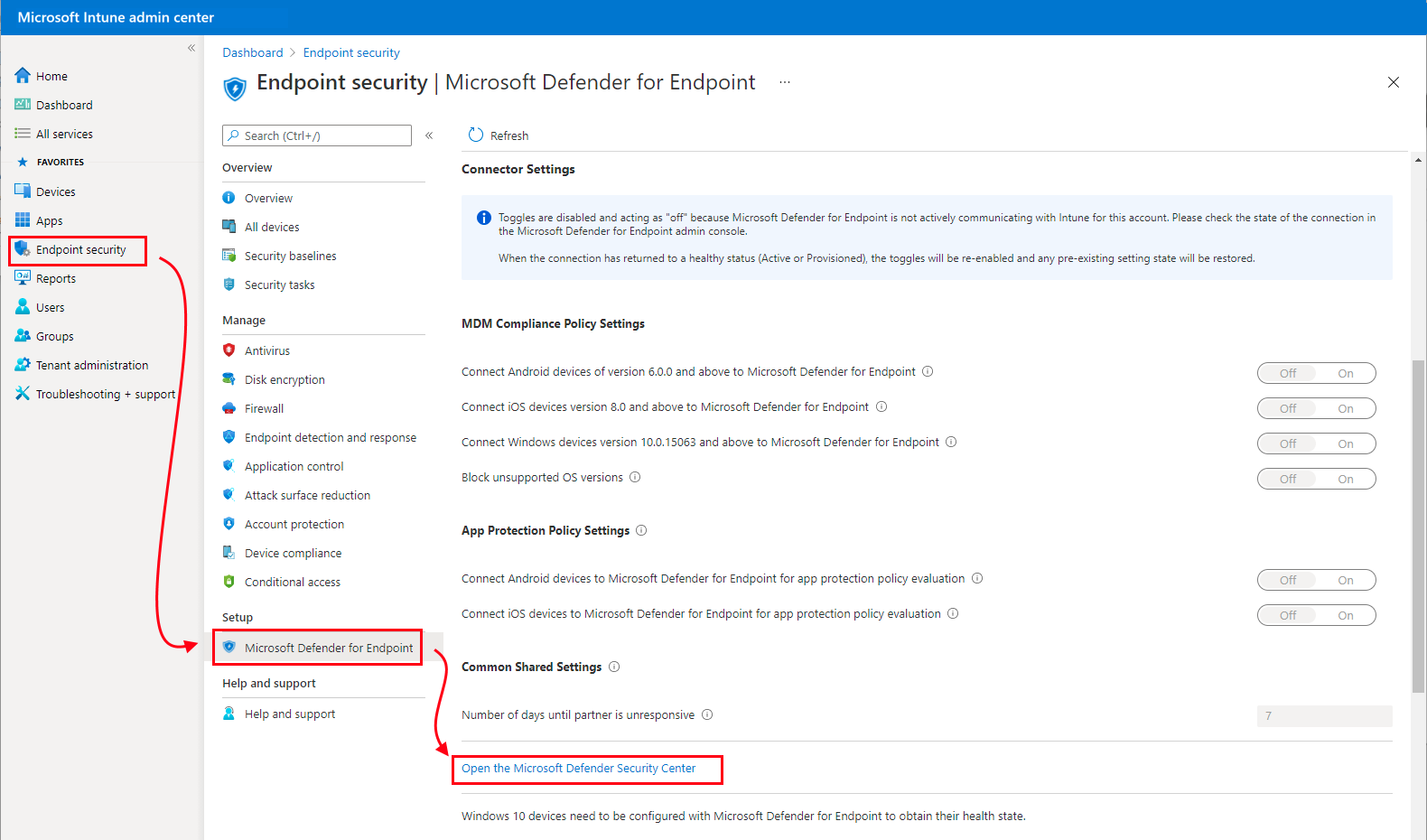
From Devices | Overview, select Configuration Profiles (under Policy heading). This is a great place to start, if you’re new to Intune.Select Endpoint security > Microsoft Defender for Endpoint, and then select Open the Microsoft Defender Security Center.
How to Customize Endpoint Security Settings in Microsoft Intune
The Managed by information is also available on the devices side .You can use the Endpoint security node in the Microsoft Intune admin center to configure and deploy endpoint security policies. Use that link to view the settings policy configuration service provider (CSP) or relevant content that explains the settings . Select Devices in the left-hand navigation pane. Step 1 – Set up Intune.Because Intune app protection policies target a user’s identity, the protection settings for a user can apply to both enrolled (MDM managed) and nonenrolled devices (no MDM).Intune supports security baselines for Windows 10/11 device settings, Microsoft Edge, Microsoft Defender for Endpoint Protection, and more.When you established the connection between Intune and Microsoft Defender for Endpoint, Intune received a Microsoft Defender for Endpoint onboarding .Does anyone know how to turn App & browser control .Endpoint detection and response – When you integrate Microsoft Defender for Endpoint with Intune, use the endpoint security policies for endpoint detection and response (EDR) to .


Create an email device configuration profile in Microsoft Intune, and deploy this profile to Android device administrator, Android Enterprise, iOS, iPadOS, and Windows devices.Endpoint Protection プロファイルにカスタム ファイアウォール規則を追加するには. Manage portal access using RBAC as well as device groups.
On April 5, 2022, the Windows 10 and later platform was replaced by the Windows 10, Windows 11, . The device configuration workload includes settings that you manage for devices in your organization.To opt in, in the Microsoft Defender portal, choose Settings > Endpoints > Advanced features > Tamper protection. The policy settings that are described can be configured for an app protection policy on the Settings pane in the portal when you make a new policy. However, device configuration policies don’t support tenant attached devices. Das Intune Admin Center enthält auch einen Link zum Defender für Endpunkt-Portal.systemcenterdudes. Unified endpoint security using Microsoft Endpoint Manager. Published May 26 2020 06:15 AM 23K Views. For some tasks, Intune requires unauthenticated proxy server access to manage. With Intune, you can use device configuration profiles to manage common Endpoint protection security features on .net, and graph.If you enable the setting, and then change it back to Not configured, then Intune leaves the setting in its previously configured state. As of writing this blog post, this . For more information, go to: Get started with your Microsoft Intune deployment.Device configuration. Network Inspection System (NIS): NIS helps to protect devices against network-based exploits. To access Intune, you need to sign in with your work or school . Endpoint Protection.Read on and start protecting your endpoints with Microsoft Intune! Prerequisites. You can use the Microsoft Defender XDR Device inventory to confirm a device is using the security settings management capability in Defender for Endpoint, by reviewing the devices status in the Managed by column.Configure devices for endpoint protection, provision certificates for authentication, set software update behaviors, and more. Enable the threat intel and SIEM integration. In the drop-down list below Platform, select Windows 10 and later. Zum Verwalten der Gerätesicherheit können Sie auch Endpunktsicherheitsrichtlinien verwenden, die sich direkt auf Teilmengen der . Ensure device health and compliance by using Microsoft Security signals and advanced endpoint management capabilities to mitigate cyberthreats and .
comManage Local Admin Accounts with Microsoft Intune – . In this article. To follow along, there .For this demo, I will show you how to configure almost all settings in the MEM console with the exception of making sure Intune is set to on in Microsoft Defender for Endpoint so all systems are properly synchronized. Wählen Sie Endpunktsicherheit > Microsoft Defender für Endpunkt und dann Microsoft Defender Security Center öffnen aus. On the Access to work or school page, select the connected account that should be . This article describes the settings in the device configuration Endpoint protection .Open the Settings app, and navigate to Accounts > Access work or school.Add Endpoint protection settings in Intune. Each endpoint security policy supports one or more profiles. Microsoft Defender Antivirus and PUA protection The potentially unwanted application (PUA) protection feature in Microsoft Defender Antivirus can detect and block PUA on endpoints in your .Microsoft Intune includes many settings to help protect your devices. When the Intune UI includes a Learn more link for a setting, you’ll find that here as well. Modify your general settings that were previously defined as part of the onboarding process.Strengthen security. Configure suppressions rules and automation settings. Onboard and offboard devices. With Intune, you can configure policies, .Configure Microsoft Defender for Endpoint in Intune.
Microsoft Intune でエンドポイント保護設定を構成する
Add authentication methods to connect to corporate email on .This security task appears in the Microsoft Intune admin center with a status of Pending: The Intune admin selects the security task to view details about the task. 19 contributors.
Manage endpoint security policies in Microsoft Intune
The endpoints in this article allow access to the ports identified in the following tables. These profiles are . With Intune, you can configure policies, monitor compliance, and integrate with other Microsoft services, such as Defender for Endpoint and Configuration Manager.The connector has the same network requirements as managed devices. Also consider, the backup directory must be supported by the devices join type – if you set the directory to an on-premises Active Directory and the device is not domain joined, it will accept the policy settings from Intune, but LAPS cannot . Microsoft Defender for Endpoint for macOS (In the . Policy templates can be found via Create policy > . Connect Microsoft Defender for Endpoint to Intune.comEmpfohlen auf der Grundlage der beliebten • Feedback
Protect devices with Microsoft Intune
The admin then remediates the task based on the guidance .Microsoft Intune does now have the capability to add custom firewall rules to a Windows 10 device using Endpoint Protection profiles. Use email profiles to configure common email settings, including a Microsoft Exchange email server. When using multiple polices or policy types like device configuration policy and endpoint detection and response policy to manage the .
Microsoft Intune—Endpoint Management
Microsoft Intune admin center is a cloud-based service that helps you manage and secure your organization’s devices, apps, and data. Intune doesn’t turn off this feature.Users must unenroll their devices from the current MDM provider before they enroll in Intune. When tamper protection is turned on, tamper-protected settings cannot be changed.Different baseline types, like the MDM security and the Defender for Endpoint baselines, could also set different defaults. With device compliance . Want to better secure your devices and data from cyber threats? Get the top 5 tips and features that you should .Microsoft Intune enthält viele Einstellungen zum Schutz Ihrer Geräte. In diesem Artikel werden die Einstellungen in der Endpoint Protection-Vorlage für die Gerätekonfiguration beschrieben. Even though Windows and Windows Server are designed to be secure out-of-the-box, many organizations still . Switching this workload also moves the Resource Access and Endpoint Protection workloads.
Microsoft Endpoint Manager: Enable Endpoint Protection
If you’re using Microsoft Intune to manage Defender for Endpoint settings, make sure to set DisableLocalAdminMerge to true on devices. This tutorial comprises hands-on demonstrations.
Network endpoints for Microsoft Intune
Melden Sie sich beim Microsoft Intune Admin Center an. The admin then selects Accept, which updates the status in Intune, and in Defender for Endpoint to be Accepted.Sign in to the Microsoft Endpoint Manager portal. Including how to change .What to expect in the Microsoft Defender portal. Intune管理センターで、Microsoft Defender for Endpoint ページの上部にある [接続の状態] が既に [有効] に設定されている場合、Intuneへの接続は既にアクティブであり、管理センターにはリンクの異なる UI テキストが表示されます。 このイベントでは、[Microsoft Defender for Endpoint管理コンソールを . This article describes the app protection policy settings for iOS/iPadOS devices.Öffnen Sie das Microsoft Defender for Endpoint-Portal unter security. When you create a profile ( Configuration > Create ), choose your platform: Then, choose the profile. Defender/AllowBehaviorMonitoring CSP.Microsoft Intune and Configuration Manager. Prerequisites for .Find the endpoint security policies for Account protection under Manage in the Endpoint security node of the Microsoft Intune admin center.Microsoft has unveiled all the new features it introduced in Microsoft Intune during the month of March 2024.
Configure Microsoft Defender for Endpoint in Microsoft Intune
When you enable tamper protection in the Microsoft Defender portal, the setting is applied tenant wide and restricts tamper-protected settings to their secure defaults. LAPS on Windows devices can be configured to use one directory type or the other, but not both.The top 5 tips for endpoint security with Intune. You can still deploy settings from Configuration Manager to co-managed devices even though Intune is the device configuration authority. With that said, let’s get started and see MEM’s awesome capability of the Endpoint Security tab and start protecting your . To avoid breaking management experiences, including Intune (and Configuration Manager), keep in mind . Set up Intune, including setting the MDM Authority to Intune.新しい設定形式を使用するプロファイルの場合、Intune は名前で各設定の一覧を保持しなくなりました。 代わりに、各設定の名前、その構成オプション、およびMicrosoft Intune管理センターに表示される説明テキストは、設定の権限のあるコンテンツから直接取得されます。 そのコンテンツは . You can use attack surface reduction (ASR) policies to reduce the attack surface of devices by minimizing the places . In Microsoft Defender Security .comEmpfohlen auf der Grundlage der beliebten • Feedback Endpoint security policies migrating to the unified settings platform in Microsoft Intune.In this section. Deploy apps and create app protection policies.
- Englisch Can Can’T Übungen – Englische Grammatik
- Energiesparhaus Nachhaltig Bauen
- Energy Sachsen Frequenz _ ENERGY Sachsen
- Engagement Rechner Instagram _ Instagram Money & Engagement Calculator
- Endpoint Security Für Mac | Unternehmens-Schutz: 17 Endpoint-Lösungen für Windows im Test
- Emz Mosel Zeitung Todesanzeigen
- Englisch Grammatik Liste , Unregelmäßige Verben Englisch (Irregular Verbs)
- Energieausweis Bei Immobilienverkauf
- Energy Exercises For Weight Loss
- Engl Jagdhund Rätsel : englischer Jagdhund mit 6 Buchstaben • Kreuzworträtsel Hilfe
- England Shirts For Women , London T Shirts for Women