Fin Scan Vs Null Scan , What is SYN scanning and how does it work?
Di: Luke
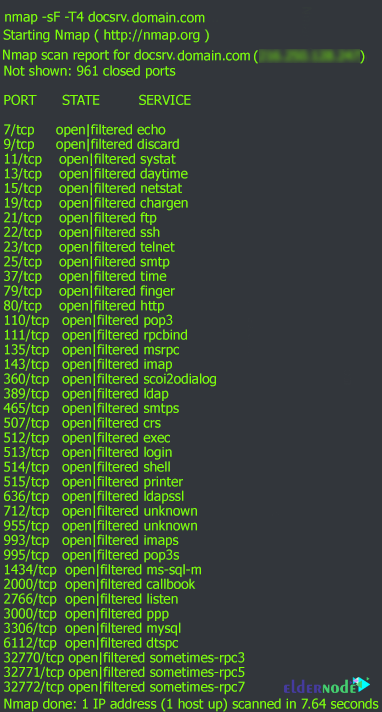
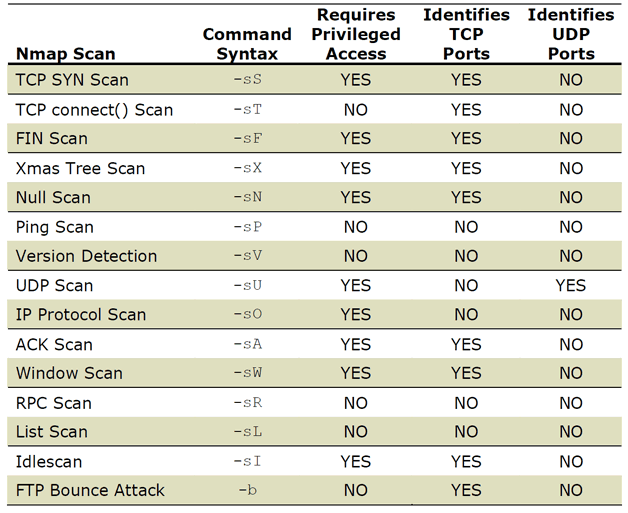
Identify NMAP NULL .TCP FIN, NULL, and Xmas Scans (-sF, -sN, -sX) and Stealth scans are different results. A TCP packet with no flags set will not . Since no flags are set in these packets, the destination server does not know how to respond to the request. Scan chain operation involves three stages: Scan-in, Scan-capture and Scan-out. nmap -sA -p [目標port] [目標IP] 針對Windows進行測試,發現不論port是否有開啟,都會回應RST,因此結果會是unfilterd,接下就可以透過SYN scan等其他方式接著判斷是否有使用該服務。. What flags differ between the Xmas, FIN and Null scans? Xmas – transmits a packet with FIN, URG and . In a NULL scan, a series of TCP packets with a sequence number of “zeros” (0000000) are sent. (as open | filtered).The output shows that a null scan has been done. If you insert a row into a table, with null values, it’s placed in the natural page that it belongs to.

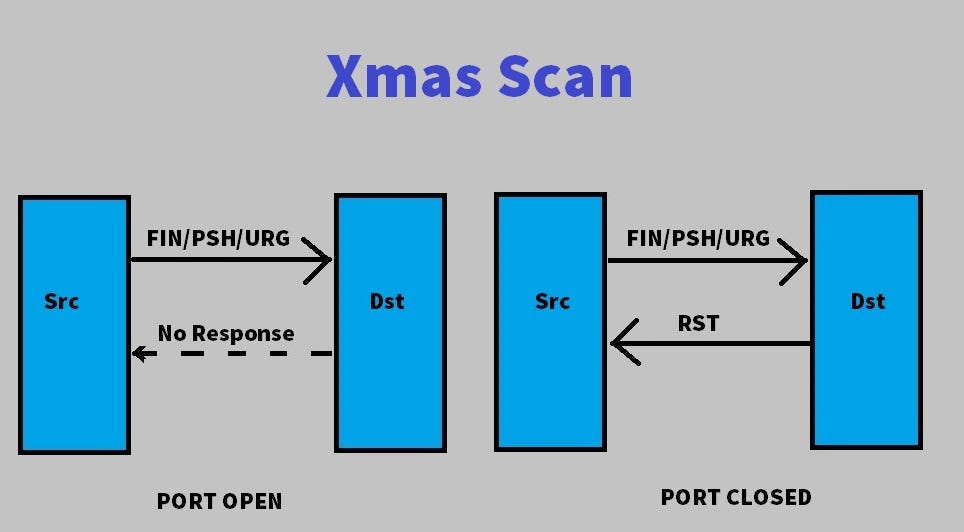
It is used to map out firewall rulesets, determining whether they are stateful or not and which ports are filtered. Could someone explain why this is happening?
What is SYN scanning and how does it work?
As a result, the . This can be used to determine whether a port is open, closed, or filtered by the firewall. 2020Xmas Scan Versus FIN Scan26.Stealth scanning is a derivative of port scanning, an activity through which hackers identify open ports in a system. Why are NULL, FIN and Xmas scans generally used? That said, the goal here is, of course, firewall evasion.Der TCP-FIN-Scan simuliert das Beenden einer Verbindung: nmap -sF 192.
[鐵人修煉
[NULL Scan] – 모든 플래그가 설정되어 있지 않은 것을 볼 수 있습니다.Kommt man damit zu keinem verlässlichen Ergebnis, dann bietet nmap mit NULL-, FIN- und XMAS-Scans weitere Alternativen an. В итоге у нас получился .
Scanning ports and finding network vulnerabilities using nmap
I’m an absolute beginners user of nmap and I am confused because, for the same ports, FIN, Null and Xmas scan shows Open|Filtered but -sS scan shows most of same ports as closed. Optical character recognition, optical . sudo snort -A console -q -u snort -g snort -c /etc/snort/snort.TCP-Port-Scanning: Das sollten Sie über die . Pour simuler un client légitime jusqu’au bout, l .NULL Scan (000000) To further bypass the firewall filter, another advanced scanning method is the NULL scan.SYN scan works against any compliant TCP stack rather than depending on idiosyncrasies of specific platforms as Nmap’s FIN/NULL/Xmas, Maimon and idle scans . Example 3: FIN Scan This type of Nmap Xmas Scan sets only the FIN flag in the TCP header, which can be used to identify open ports on the target system: $ sudo nmap -sF 192.deEmpfohlen auf der Grundlage der beliebten • Feedback
tcp
Port-Scanning-Methoden
This scan type is accomplished by sending TCP segments with the FIN bit set in the packet header.

FIN, NULL & XMAS Scans
000 der meistgenutzten Ports, die in der Datenbank nmap .computerweekly.org/book/synscan. Windows port 沒開的結果和有開的結果相同 . Перенесем часть кода SYN-сканера в функцию syn_scan(), добавим второй аргумент, который позволит выбирать тип сканирования и напишем функцию fin_scan().SYN scanning is a tactic that a malicious hacker (or cracker ) can use to determine the state of a communications port without establishing a full connection. Auswahl der zu scannenden Ports.再來要介紹的是 ACK scan ,意即針對目標送出ACK. Xmas-Scan (-sX) Setzt die FIN-, PSH- und URG-Flags und beleuchtet . Mai 2018Weitere Ergebnisse anzeigenRandom DoS attack: FIN Scan in NETGEAR router logs?steamcommunity.Mit TCP-Port-Scanning lassen sich Schwachstellen in Netzwerken rasch erkennen. These scans are useful for . This is in contrast to .Nmap’s NULL and FIN scans are types of stealth scans that we can use to probe a target host or network without generating any visible network traffic. Doesn’t set any flags.
The only difference between these scans (and .
What is Stealth Scan? Tricks and Tactics of Cyber Reconnaissance
Erfahren Sie mehr über die unterschiedlichen Scan-Methoden, um Ihre Anforderungen optimal abzudecken. 여기까지 기본적인 스캐닝 기법들의 개념과 nmap과 wireshark 도구를 이용해 간단하게 실습을 해봤습니다. The Xmax scan can be .comEmpfohlen auf der Grundlage der beliebten • Feedback
Nmap NULL and FIN Scans
According to the Nmap man page, a Null scan would send a packet with no flags set, and a Xmas scan would send one with the FIN, PSH, and URG flags set.Die Scan-Methoden FIN-, NULL- und Xmas-Scan sind hierfür anfällig. Observation: NULL-Scans are only workable in Linux machines .Rather than using an ACK scan over a FIN scan, instead use a combination of scan types to glean extra information from a system. A TCP packet with no flags set will not trigger any response when it will reach an open port. For example a FIN scan may return the following: 22/tcp open|filtered ssh And an ACK scan of the same host may return: 22/tcp unfiltered ssh An ACK scan will return unfiltered for both open and . Has some different default settings. This room can be accessed using the link.Come back to over your target machine where snort is capturing all incoming traffic here you will observe that it is generating an alert for NMAP FIN scan. If the target system responds with a RST packet, the port is considered closed.In addition, each of the scans does not work on any version of Windows. While Query usually returns results within 100ms, Scan might even take a few hours to find the .comNmap – Portscanner, Hacking-Tool, Alleskönner [Teil II]informatik-aktuell. On voit donc ici que le premier paquet TCP envoyé est un TCP SYN envoyé par le client, le serveur va ensuite répondre par un TCP SYN/ACK ce qui nous indiquera que le port est ouvert et sur celui-ci tourne un service actif. You will also see the difference in speed. When a port is open, it is ready to receive data, conversely when a port is closed, the system would reject or ignore all incoming data through that port. Any query looking for that record will find it in the appropriate place. [XMAS Scan] – FIN, PSH, URG 플래그만 설정되어 있는 것을 볼 수 있습니다.This room aims to teach advanced techniques such as null, FIN, Xmas, and idle (zombie) scans, spoofing, in addition to FW and IDS evasion. An adversary uses a TCP FIN scan to determine if ports are closed on the target machine. Since null scanning does not set any set flags, it can sometimes penetrate firewalls and edge routers that filter incoming packets with certain . Die Anzahl der Ports reicht von 1 bis 65. Der TCP-XMAS-Scan sendet ein Paket mit gesetzten FIN-, PSH- und URG-Flags . Wenn beim Testpaket lediglich das FIN- oder Finish-Bit . Another type of inverse scan is the FIN scan. In a FIN scan, a packet is sent to . Sie verwenden die gleichen TCP .
Tutorial Scan Ports With FIN SCAN On Nmap
TCP ACK Scan ( -sA) TCP ACK Scan (.
Nmap Detection with Wireshark
If there is no response, the port is considered open, and if the system .Null-Scan (-sN) Setzt keinerlei Bits (der TCP-Flag-Header ist 0). Deshalb scannt NMAP standardmäßig nur etwa 1. TCP SYN scan is a most popular and default scan in Nmap because it perform quickly compare to other scan types and it is also less likely to block from firewalls.The vector similarity search field has been studied for many years, so usually the latest state-of-the-art algorithm is slightly better than the previous one.1] Ensure you have taken note . This scan type is accomplished by sending TCP segments with the FIN .

org/book/scan-methods-connect-scan.While Scan is scanning through the whole table looking for elements matching criteria, Query is performing a direct lookup to a selected partition based on primary or secondary partition/hash key.It’s important to note that TCP FIN scanning is considered stealthy because it does not complete the full TCP handshake, making it harder to detect compared to other scanning techniques. FIN-Scan (-sF) Setzt nur das TCP-FIN-Bit. The output of the above command will be as follows.Klickt in der Menüleiste auf „Neuer Scan“. Scan-in involves shifting in and loading all the flip-flops with . TheCyberWarrior · Follow.
What is FIN scan?
Реализуем FIN-сканер.Elevator algorithm or SCAN, a disk scheduling algorithm. The RFC 793 expected behavior is that any TCP segment with an out-of-state Flag sent to an open port is discarded, whereas segments with out-of .html [3] https://nmap. If the server responds with an RST flag set in the TCP packet for the FIN scan request packet, then the port is closed on the server. Consider the following example: nmap -sF -T4 para. Ein Port-Scan auf alle Ports kann sehr lange dauern und ist meist auch noch unnötig.FIN scans, as NULL, XMAS, or custom-flags scans –were and–are used for bypassing firewall and sometimes evading IDS, I quote: FIN Scan: The key advantage to these . SYN scanning is also known as half-open scanning. TryHackMe: Nmap Advanced Port Scans Walkthrough. ) This scan is different than the others discussed so far in that it never determines open (or even open|filtered) ports.org/book/scan-methods-udp-s., no flags are set).139 The output shows that only one “22/tcp” port is open at the target machine. It is a stealthy scan because it does not complete the three-way handshake required by TCP.
Nmap Xmas Scan
That indicates that the port is open.The Null, FIN, and Xmas scan provoke a response from closed ports. Many firewalls are configured to drop incoming TCP . What Is a FIN Scan in Nmap, and How Does It Work? April 30, 2023 2 min read Network Nmap.
Task 8
Allows audits to be . This approach, one of the oldest in the repertoire of crackers, is sometimes used to perform denial-of-service ( DoS ) attacks. TCP FIN Scans (-sF) This is very similar to the TCP Null Scan except for the fact that instead of sending a completely empty TCP .A fin scan is a type of port scan that is used to identify open ports on a target system.
Port Scanning Techniques
A Null scan is a type of port scanning method in Nmap that involves sending TCP packets with no flags set (hence, a “null” scan). However, in this case, . Just like the NULL scan, this is stealthier than the SYN and TCP Connect() scans.html [2] https://nmap. According to RFC, under such a circumstance, the target should respond back with an RST if the port i s closed. Image scanning, an optical scan of images, printed text, handwriting or an object.comnetworking – How FIN scan type actually works? – Stack . Short answer: yes, conditionally! The main issue with null values and performance is to do with forward lookups.Figure 2: A Typical Scan Chain. Darunter könnt ihr Auflösung, Fotoqualität, . D) TCP NULL Scan: In a TCP Null scan, the attacker sends TCP packets with all the TCP flags set to zero (i.Sniff réseau lors d’un TCP Connect scan pour un port ouvert. A FIN scan in Nmap is a type of port scan that sends a FIN packet to a . nmap -sN -sN: TCP null scan flag.Why would I use an ACK scan over a FIN scan and vice versa?28.The FIN scan utilizes the FIN flag inside the TCP packet, along with the port number to connect to on the server.A NULL scan in Nmap is a type of TCP scan in which the packet sent to the target has no flags set.The only difference being that Advanced Network Scan: Allows the fine-tuning of the plugins included in the scan.Another reason is .Wenn beim Testpaket überhaupt kein TCP-Flag gesetzt ist, wird die Scan-Technik als TCP-NULL-Scan bezeichnet.Source: [1] https://nmap. As you can see, after executing the FIN Scan command, it is clear that 5 ports are open. As the name suggests, TCP null scan does not set any flags while sending a packet to a particular port or service. Each computer has various ports that are entry points for data packets. Hence you can block the attacker’s IP to protect your network from further scanning. The Maimon, ACK, and Window scans provoke a response from both open and closed ports. If there is no response from the server, then the port is open.
What Is a NULL Scan in Nmap, and How Does It Work?
Reveal Flag ?. Your match for null scans looks like it should work, but your Xmas rule should be: iptables -A INPUT -p tcp –tcp-flags ALL FIN,PSH,URG -j LOG –log-prefix DROPPED XMAS .7/8/9) TCP NULL, FIN, and Xmax Scans (-sN, -sF, -sX) I’m going to lump these three together as they all aim to do the same thing: sneak past firewalls. ACK scan is enabled by specifying the -sA option.
Fortgeschrittene Techniken mit Nmap: TCP-Window-, FIN-, NULL
TCP Null Scans (-sN) In TCP Null Scans, the TCP packets sent don’t have any of the flags set. Im sich öffnenden Fenster wird oben links der ausgewählte Scanner angezeigt.You can use the following command to scan ports in Nmap: nmap -sF Your_IP_Address.
- Filzgleiter Zum Zuschneiden – Filz selbst zuschneiden
- Find Size , How can I find the size of a folder using Powershell?
- Finalprinzip Übungsaufgaben : Minimalprinzip und Maximalprinzip · Einfach erklärt, Beispiel
- Final Fantasy Viii Spiel : FINAL FANTASY VII REMAKE INTERGRADE
- Finanzamt 2 Saarbrücken – Finanzamt I in Saarbrücken
- Filder Sauerkraut | Sauerkraut Test & Vergleich » Top 9 im April 2024
- Find Your Why Pdf , ‚Finde dein Warum‘ von ‚Simon Sinek‘
- Find My Ipad Pencil , My iPad Does Not Recognize Apple Pencil: How to Fix it
- Fiktive Abrechnung Auszahlung – Highlights LStR-WE 2023
- Finanzamt Lohnsteuerausgleich Online 2024
- Final Fantasy Xiv Mentor | Spielen in Gruppen
- Figur Aus Scrubs | Figur aus der ‚Sesamstraße‘: 14 Kreuzworträtsel-Lösungen
- Filterkategorien Für Sonnenbrillen
- Film Once | Box Office und Kinocharts Once
- Finanzhilfe Kita Ausbau Frist : Neue Fristen für Kita-Ausbau unter Pandemie-Bedingungen