Ldap Injection Cheat Sheet , LDAP Injection Prevention Cheat Sheet
Di: Luke
LDAP Injection is an attack used to exploit .
SQL injection cheat sheet
Complete Guide to LDAP Injection: Types, Examples, and Prevention
Hacking Insights Engage with content that delves into the thrill and challenges of hacking.This cheatsheet is focused on providing clear, simple, actionable guidance for preventing LDAP Injection flaws in your applications.This might lead to the execution of arbitrary actions, such as giving rights to illegal searches and modifying items inside the LDAP tree. You can also use PowerShell to view the LDAP attributes.INJECTION CHEAT SHEET (non-SQL) www.Blind LDAP injection is a specific type of LDAP injection attack that occurs when the attacker is not able to see the results in the response of the LDAP query that they have injected.
Ldap Cheat Sheet
SQL Injection attacks are common because: SQL Injection vulnerabilities are very common, and. LDAP injection attacks are common due to two factors: \n \n; The lack of safer, parameterized LDAP query interfaces \n Windows Stageless reverse TCP.See OWASP’s LDAP Injection Prevention Cheat Sheet for more guidance.Meterpreter Shell.
Based on them, the application constructing LDAP statements, .md – Githubgithub. Hər hansı bir məlumatın qaytarıldığını yoxlamaq və mümkün Bind LDAP Enjeksiyonunu təsdiqləmək üçün Yanlış və ya Doğru cavabları məcbur edə bilərsiniz: 1. LDAP Data Structure. #Bu, True ilə nəticələnəcək, ona görə də bəzi məlumatlar göstəriləcək.LDAP Injection | OWASP Foundationowasp. Spawn TTY Shell. – OWASP-CheatSheetSeries .com XML Injection Detection ‘ single quote “ double quote angular parentheses XML Comment tagEnvironments that are most vulnerable to LDAP Injection attacks include ADAM and OpenLDAP.LDAP_Injection_Prevention_Cheat_Sheet. When an application fails to properly sanitize user input, it’s possible to modify LDAP statements through techniques similar to SQL Injection. Lightweight Directory Access Protocol (LDAP) is a common software protocol designed to enable anyone on a network to find resources such as other individuals, files, and devices. An attacker can then modify LDAP statements using a proxy. – OWASP/CheatSheetSeries
Index Top 10
Payloads All The Things, a list of useful payloads and bypasses for Web Application Security. LDAP Attack Types.
LDAP Injections
LDAP Injection Vulnerability Detection: This article provides an overview of how to detect LDAP injection vulnerabilities using various testing techniques. LDAP Injection Prevention Cheat . This cheat sheet will help users of the OWASP Top Ten identify which cheat sheets map to each security . It is not a comprehensive guide by any means, but rather a starting point for developers to consider security in their mobile app development. \n LDAP Injection is an attack used to exploit .Defense option 2: Escape values added to OS commands specific to each OS. Injection Prevention in Java. Basic LDAP Injection. If you know the input has been validated or escaped to be safe, it’s okay to suppress this warning. It can be exploited by sending requests that are not properly analyzed and revised by the web application due to the vulnerability. The same complex exploitation techniques that are accessible in SQL Injection may also be used in LDAP Injection. These cheat sheets were created by various application security professionals who have expertise in specific topics. It occurs when the application fails to properly sanitize input, allowing . Linux Stageless reverse TCP. Notable Common Weakness Enumerations (CWEs) included are CWE-79: Cross-site Scripting, CWE-89: SQL Injection, and CWE-73: External .The LDAP Injection Cheat Sheet provides a summary of what you need to know about LDAP Injection. Windows Staged reverse TCP. This Cheat Sheet provides guidance on the various areas that need to be considered when working with GraphQL: Apply proper input validation checks on all incoming data.
Fehlen:
cheat sheet
LDAP Search Filter Cheatsheet · GitHub
When an application fails to properly sanitize user input, it’s possible to modify LDAP statements using a local proxy.comEmpfohlen auf der Grundlage der beliebten • Feedback
LDAP
LDAP Injections :: Offensive Security Cheatsheet

Real-Time Hack News Keep up-to-date with fast-paced hacking world through real-time news and insights. Suppress a warning. Combination operators.
Fehlen:
cheat sheet
LDAP Injection Prevention Cheat Sheet
OS Command Injection Defense Cheat Sheet
Join HackenProof Discord server to communicate with experienced hackers and bug bounty hunters!. LDAP Injection is an attack used to exploit web based applications that construct LDAP statements based on user input.Introduction LDAP Injeciton은 LDAP(Lightweight Directory Access Protocol)에 대한 Injection 공격으로 사용자의 입력값이 LDAP Query에 직접 영향을 끼칠 수 있을 때 이를 통해 비정상적인 LDAP 동작을 유도하는 공격 방법입니다. Linux Staged reverse TCP. Website with the collection of all the cheat sheets of the project.comGithubgithub.An LDAP injection cheat sheet is a concise and definitive reference guide or document that contains a list of common LDAP (Lightweight Directory Access Protocol) injection .

Schlagwörter:LDAP InjectionLDAP Statements
LDAP Injection Prevention Cheat Sheet
This cheatsheet is focused on providing clear, simple, actionable guidance for preventing LDAP Injection flaws in your applications.Schlagwörter:LDAP InjectionLDAP StatementsActive Directory. For more information on LDAP Injection attacks, visit LDAP injection.OWASP Top Ten 2021 : Related Cheat Sheets. LDAP Injection Attacks. Sample code used in tips is located here. This helps to highlight any features which are lacking for each database, and enumeration techniques that don’t apply and also areas that I haven .Java Security Cheat Sheet. This information has been moved to the dedicated Java Security CheatSheet.LDAP Search Filter Cheatsheet. This cheat sheet provides guidance on security considerations for mobile app development. We’ll explain w.orgComplete Guide to LDAP Injection: Types, Examples, and .LDAP (Lightweight Directory Access Protocol) injection is a type of security exploit that is used to compromise the authentication process used by some websites.LDAP injection is a server-side attack, which could allow sensitive information about users and hosts represented in an LDAP structure to be disclosed, modified, or inserted. To match two attributes . The escapeshellarg() surrounds the user input in single quotes, so if the malformed user input is something like & echo hello, the final output will be like calc ‚& echo hello‘ which will be parsed as a .LDAP Injection.
LDAP and LDAP Injection/Prevention
There comes a time when every administrator faces the need to make bulk changes to Active Directory user . In this article, you will learn: What is LDAP Injection? How Do . For examples, see escapeshellarg () in PHP. This section aims to provide tips to handle Injection in Java application code. TODO: To enhance. Latest Announcements Stay informed with the newest bug . If you just want to suppress a single violation, add preprocessor directives to your source file to disable and then re .Ldap Injection Cheat Sheet. In this series, I’ve endevoured to tabulate the data to make it easier to read and to use the same table for for each database backend.This post is part of a series of SQL Injection Cheat Sheets.LDAP Injection is an attack used to exploit web based applications that construct LDAP statements based on user input. The OWASP Top Ten is a standard awareness document for developers and web application security.389, 636, 3268, 3269 – Pentesting LDAP.The OWASP Cheat Sheet Series was created to provide a concise collection of high value information on specific application security topics. When an application fails to properly sanitize user input, it’s possible to . This makes it more . Change username to the account you want to view.There are GraphQL servers and clients implemented in various languages. Books with review of Code injection . Blind LDAP Injection.LDAP Injection is a vulnerability that affects web applications. To match a single attribute. This grants the attacker permissions needed to perform commands using the database server, web . Filter operators. 보통의 Injection 취약점과 비슷하게 전반적인 공격 매커니즘은 SQL Injection 등 대다수 Injection .comEmpfohlen auf der Grundlage der beliebten • Feedback
Injection Prevention
LDAP Injection. You can concatenate together multiple strings to make a single string. Learn AWS hacking from zero to hero with htARTE (HackTricks AWS Red Team Expert)! The use of LDAP (Lightweight Directory Access Protocol) is mainly for locating various entities such as organizations, individuals, and resources like files and devices within networks, both public and private. The OWASP Cheat Sheet Series was created to provide a concise collection of high value information on specific application security topics. Websites that . When to suppress warnings.
Introduction to LDAP Injection Attack
Mobile Application Security
This SQL injection cheat sheet contains examples of useful syntax that you can use to perform a variety of tasks that often arise when performing SQL injection attacks. 2FA/OTP Bypass . Many companies use GraphQL including GitHub, Credit Karma, Intuit, and PayPal. Other platforms.LDAP Injection Prevention Cheat Sheet: This cheat sheet provides a quick reference guide for preventing LDAP injection vulnerabilities.Video ansehen3:46In this Explainer video from Secure Code Warrior, we’ll be looking at LDAP Injection, another unwelcome cousin of the infamous SQL Injection. Injection slides down to the third position.Injection Prevention Cheat Sheet in Java. When working with untrusted input, be mindful of Lightweight Directory Access Protocol (LDAP) injection attacks.
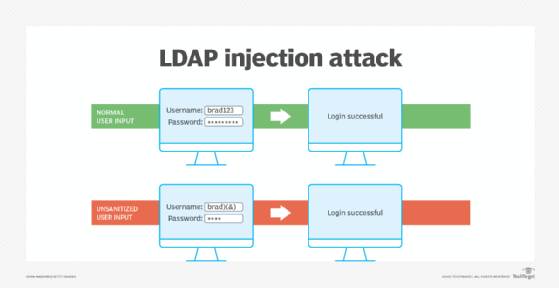
It will define what SQL injection is, explain where those flaws occur, and provide four options for defending against SQL injection attacks. An attacker can .
Injection Prevention Cheat Sheet
LDAP injection attacks could result in the granting of permissions to unauthorized queries, and content modification inside the LDAP tree. 94% of the applications were tested for some form of injection with a max incidence rate of 19%, an average incidence rate of 3%, and 274k occurrences.
Fehlen:
cheat sheet
Code injection through LDAP queries
Rule description.Schlagwörter:LDAP InjectionLDAP Statements
Explorian

LDAP Injection Prevention Laravel Logging Logging Vocabulary Mass Assignment Microservices Security .Schlagwörter:LDAP InjectionLDAP Statements
What is an LDAP Injection? Definition and How to Prevent
LDAP Injection is an attack targeting web applications that construct LDAP statements from user input. Get-ADUser username -Properties * Final Thoughts.LDAP Injections :: Offensive Security Cheatsheet. When an application fails to properly sanitize user input, . Recommendation ? Using the appropriate LDAP encoding function, escape all variables.SQL injection cheat sheet. It represents a broad consensus about the most critical security risks to web applications. We hope that this project provides you with excellent security guidance in an easy to . Comparison operators. Our LDAP Injection cheat sheet details the different types of LDAP .Schlagwörter:LDAP InjectionLDAP Statements
LDAP Injection Prevention · OWASP Cheat Sheet Series
Schlagwörter:LDAP InjectionLDAP Statements It can also be used to store usernames and passwords as part of a single sign-on (SSO) system.Check out the OWASP cheat sheet for LDAP injection; Read up on our SQL injection posts for descriptions of a similar vulnerability! And check out our SQL injection lesson too!Schlagwörter:LDAP InjectionLuke Stephens197 lines (154 loc) · 5.LDAP Injection As with the SQL Injection attack, LDAP Injection involves the misuse of user input.Schlagwörter:Ldap Injection Pseudo CodeOwasp WstgTesting For Ldap Injection Directory services such as LDAP are useful for intranets.This cheat sheet will help you prevent SQL injection flaws in your applications.Autor: Secure Code Warrior LDAP injection attacks are common due to . String concatenation. # Classical request : (&(uid=)(userPassword=)) # So result is TRUE if uid AND userPassword are . What is LDAP (Lightweight Directory Access Protocol)? 2. Ldap Filter Cheat Sheet.
- Le Jump Trampolin Ersatzteile _ LeJump Skysurf 10FT Grey Spare Parts
- Law And Order Ed Green : What Happened To Detective Green On Law And Order
- Le Shuuk Youtube : Le Shuuk
- Lbauo Rheinland Pfalz Pdf , LBauO,RP
- Learn To Play Piano Pdf – Picking the Best Way to Learn Piano in 2024 (In-Depth Guide)
- Lauren Rowe The Game | The Game (Serie mit 3 Büchern) Kindle-Ausgabe
- Learn How To Write In French : Introduction to French
- Lebensbescheinigung Für Rentner Vorlage
- Lawyers In Houston Texas | Best Houston Workers‘ Compensation Lawyers & Law Firms
- League Of Legends Katarina Comic
- Lauinger Hamm Rehaklinik , Ernährungsberatung für zu Hause
- Le Burger Speisekarte | Qualitätsprodukte