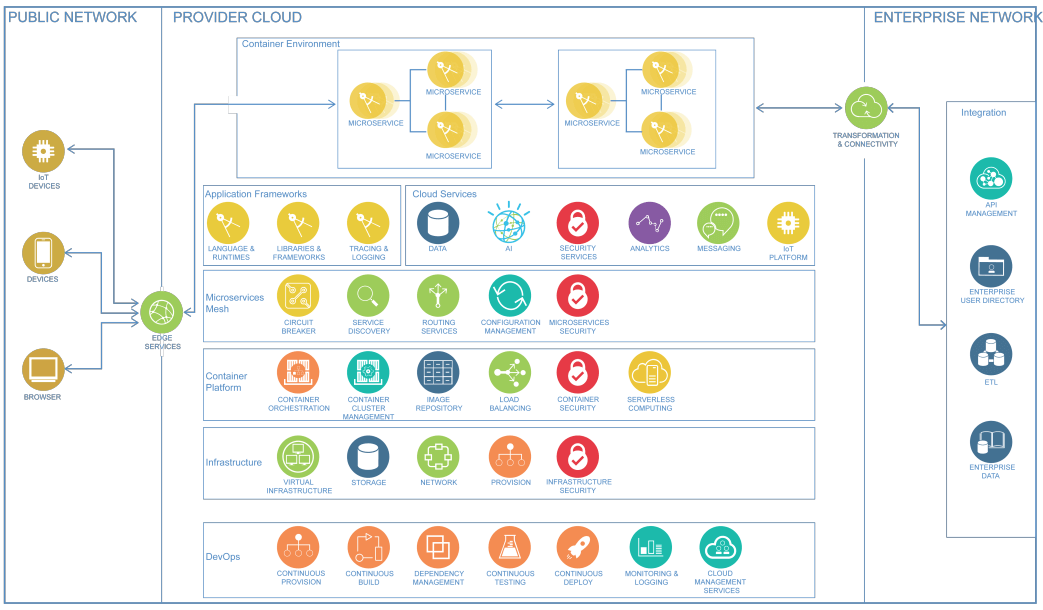
Secure Microservices Architecture
Di: Luke
Defense in Depth: Implement multiple layers of security controls at different levels of your microservices architecture. Make your microservices architecture secure by design. Quick Summary: Microservices architecture provides flexibility, scalability, and the ability to add, remove, or modify software components without . Learn how to build each layer of a multilevel .Microservice security is the strategy that development and security teams use to minimize the risks associated with microservices application architecture. Service-based architecture has become an .8 Ways to Secure Your Microservices Architecture | Oktaokta.According to Wikipedia, Microservices are a software development technique – a variant of the service-oriented architecture (SOA) architectural style that structures an application as a collection of loosely coupled services. Much like construction workers need to strategically layer rebar and concrete to build strong foundations for .Microservices architecture comes with its own security considerations. This security effort . Managing data layers is a challenge for microservices security because microservices rely on distributed data storage, which can make it challenging to ensure consistent data security across all services. API Security: Secure your APIs with proper authentication mechanisms (such as OAuth2 or . Observing it in afunctional way, it is correct to claim that it breaks down . All-in-one authentication service — The authentication service verifies users‘ identities and creates a session, issuing an identity token. With their widespread adoption, more and more work investigated the relation . These services have their own business logic and database with a specific goal.
An architect’s guide to microservices security
In the following blog, review these microservices architecture patterns and note how many are able to work together to form a secure cloud system.Microservices Architecture.It serves as an additional security check for all accessed resources, preventing security gaps and blind spots. Implement authentication in .The microservice architectural style is widespread in enterprise IT, making the securing of microservices a crucial issue.The secure development of microservices relies on architecture patterns. Use HTTPS everywhere. Secure RSocket Endpoints. It acts as a single entry point for all incoming and outgoing . An application built on a microservices architecture has: Loosely Coupled Service s: Each . Every service verifies tokens and gets additional user info separately.As the name implies, a microservices architecture is an approach to building a server application as a set of small services. And, as we have seen, these boundaries are exactly the sort of place where security vulnerabilities can often be found. All these magic works by using Node.10 November 2021. Think Strategy: How To Secure Microservices. This content is an .
Securing modern API- and microservices-based apps by design
Many bad practices in securing .
Microservices Architecture: A Comprehensive Guide
First Online: 22 December 2022.If you decide to use microservices, you need to ensure that you are meeting all the security demands for the services, connections, and data. The increasing trend in building microservices-based applications calls for addressing security in all aspects of service-to-service interactions due to their unique characteristics.Three options to implement secure authentication and authorization patterns in the secure microservices architecture are as follows.

The source code for this tutorial is available on GitHub, in the “oauth” branch.com15 Best Practices for Building a Microservices Architecturebmc. Make your microservices architecture secure by design Much like construction workers need to strategically layer rebar and concrete to build strong foundations for skyscrapers, developers must embed layers of security in applications to protect the data they hold. Microservices Authentication Challenges. Be Secure by Design. Use access and identity tokens.Securing microservices. Scan for dependencies. A microservices security plan involves managing numerous interdependent parts and a large attack surface for applications.Microservices architecture has become a popular approach to building large-scale applications. The distributed cross-domain nature of microservices needs secure token service (STS), key management and encryption services for authentication .Securing each independent service in a microservices architecture is crucial for DevOps teams. Without careful oversight, this can take the potential for unexpected dangerous behavior .Microservices are a software architecture style that structures an application as a collection of loosely coupled services designed to implement a specific .Microservices are a popular architectural style for building applications that are resilient, highly scalable, independently deployable, and able to evolve quickly. Use HTTPS Everywhere. Azure Bastion provides secure remote desktop protocol (RDP) and secure shell (SSH) access to VMs in the virtual networks by using a secure socket layer (SSL), without the need to expose the VMs through public IP addresses.Target Architecture of Identity Server with Microservices Reference Application.Microservice architectures (MSA) are becoming trending alternatives to existing software development paradigms notably for developing complex and distributed . This level of risk requires a concerted defense-in-depth strategy, which covers monitoring, logging, tracing and threat detection.
This tutorial shows you how to use Spring Security with OAuth and Okta to lock down your microservices architecture. You might remember a similar post I wrote back in August: Secure a Spring Microservices Architecture with Spring Security, JWTs, Juiser, and Okta.13 Best Practices to Secure Microservices – Geekflaregeekflare. Let us now have a look at some effective .There are more secure approaches with this architecture in which both the API gateway as well as individual microservices are secured with OAuth 2.Best Practices For Securing Microservices with Spri ng Security. That means a microservices architecture is mainly oriented to the back-end, although the approach is also being used for the front end. Step 4: Create a Project patient-management-service There is no universal model or design that can be applied to secure . The microservice architectural style is widespread in enterprise IT, making the securing of microservices a crucial issue. Authorization Servers: Many-to-One or .Managing Data Layers. Encrypt and protect secrets.
How to implement security for microservices
In this tutorial, I’ll walk you through building a secure Spring REST API that tries to solve for some of these pain points using a microservices architecture. Within microservices architecture . In a microservices architecture, data is often stored across multiple databases, caches, .What You’Ll Learn
How to Secure Microservices Architecture
Spring Security and Oauth2 Implementation in Microservices Architecture I have done OAuth2 implementation based on Spring Security. What Are Microservices? Many bad practices in securing microservices have been identified by researchers and practitioners, along with security good practices that, if adopted, allow to avoid the corresponding security issues. Each service runs in its own process and communicates with other .2 Form a security plan for microservices.Application containers and a microservices architecture are being used to design, develop, and deploy applications leveraging agile software development . A Microservice is a small or even micro independent process that communicates, acts, and returns via messages through lightweight mechanisms like Thrift, HTTP or RESTAPI.Microservices architecture has gained popularity due to its ability to break down complex applications into smaller, independently deployable services.
Authentication in Microservices: Approaches and Techniques
With Zuul, Feign, and Spring Cloud Security, you can ensure your backend services communicate securely. Much like construction workers need to strategically layer rebar and concrete to build strong foundations for skyscrapers, developers must embed layers of security in applications to protect the data they hold.As this research demonstrates, Microservices Architecture is intrinsically connected as a symbiosis with container-based deployment, because these containers .comMicroservices Security – OWASP Cheat Sheet Seriescheatsheetseries. There’s also the challenge of protecting sensitive data as it flows between services. Within microservices architecture, this means being “secure by design .A microservices architecture, also simply known as microservices, is an architectural method that relies on a series of independently deployable services.com8 fundamental microservices security best practices | .Autor: Gavin Kenny
Microservices Security
Best Practices in Implementing a Secure Microservices
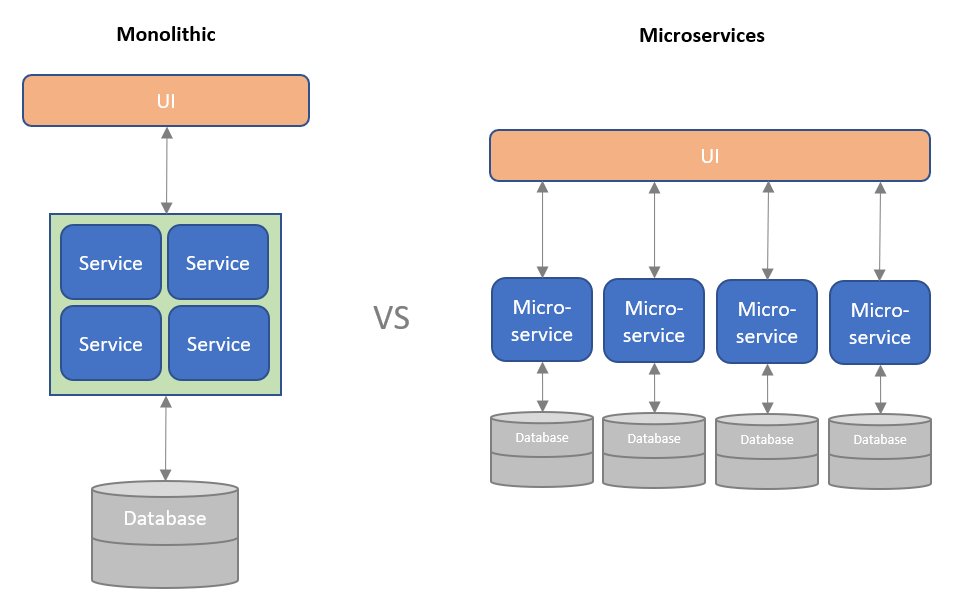
Each microservice access request must be authenticated and . API Gateway is an important component in a microservices architecture that helps manage and optimize communication between different microservices. Microservices Architecture is amateur evolution of the Monolithic Architecture. In this article, we’re going to learn how to secure microservices with using standalone Identity Server 4 and . Scan Dependencies.This includes network security, host security, application security, and data security. Microservices is an emerging paradigm for developing distributed systems. Staying Ahead of Microservices Security. In a typical microservices .Make your microservices architecture secure by design .Securing a microservices architecture involves securing each service and the communications between them.In a microservices architecture, services are fine-grained, and the protocols are lightweight.The increasing trend in building microservices-based applications calls for addressing security in all aspects of service-to-service interactions due to their unique characteristics.NET microservices and web applications. Updating, testing, deployment, and scaling occur within each service. In this article.Factors to Consider When Securing Microservices.Securing Microservices Architecture. The microservice architecture is being increasingly used for designing and implementing application systems in both cloud-based and on-premise infrastructures, high-scale applications and services. In a microservices architecture, each microservice implements a specific function or part of the business logic.
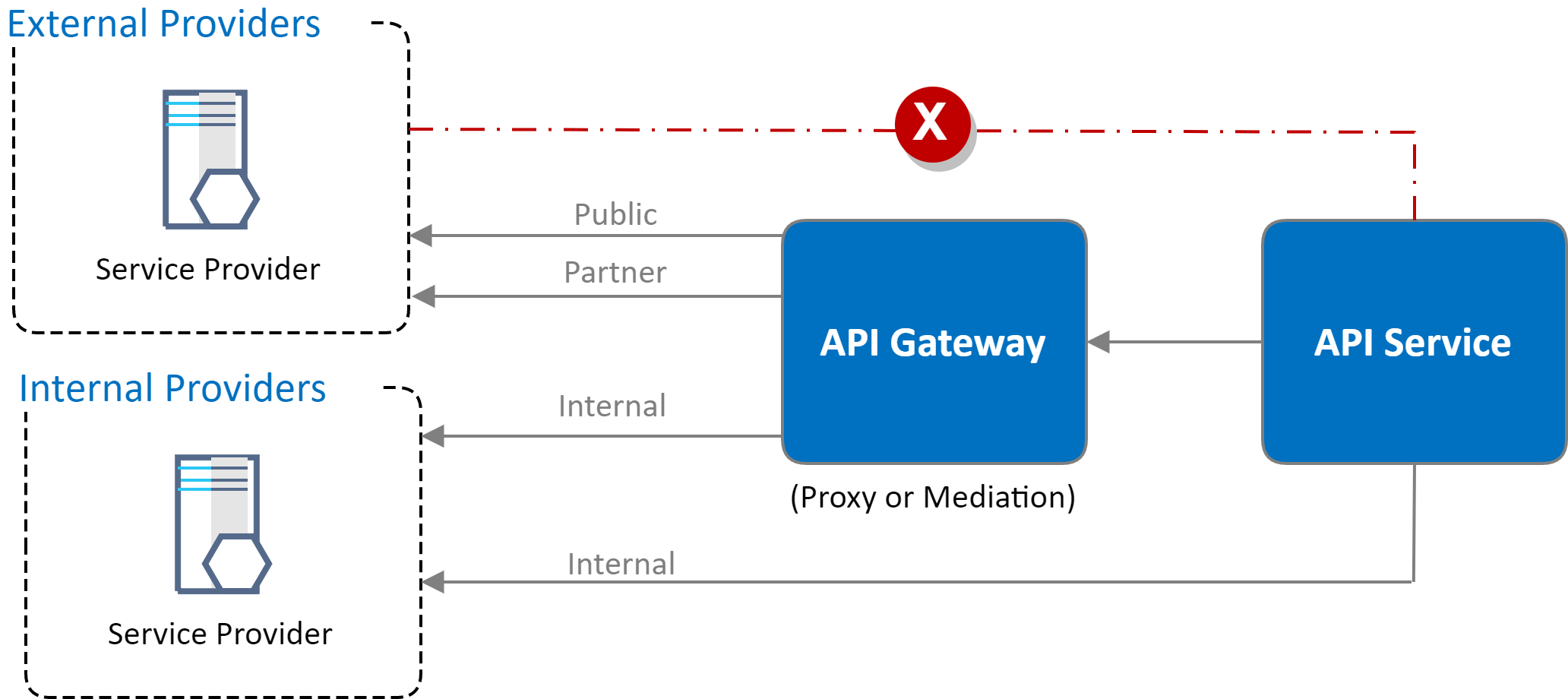
API Gateway: the Microservices Superglue
Implement API Gateway Security. Use Access and Identity Tokens.
Express Gateway is an API Gateway that sits at the heart of any microservices architecture (regardless of what language or platform you’re using), securing the different pieces and exposing them through APIs. 12 contributors.This architecture uses Azure Application Gateway Ingress Controller (AGIC) as the Kubernetes ingress controller. Implementing consistent security policies, authentication, and authorization across services adds complexity.comEmpfohlen auf der Grundlage der beliebten • Feedback
How to secure microservices: the complete guide
js, ExpressJS, and Express middleware. Secure GraphQL APIs. Key strategies include establishing robust authentication and authorization, . Key Characteristics of Microservices Architecture.integrity of your microservices architecture. Patterns and Best Practices for Microservices Security.Photo by Growtika on Unsplash. Much like construction workers need to strategically layer rebar and concrete to build strong foundations for skyscrapers, developers must embed layers of . In the following blog, review these microservices architecture patterns and note how many are able to work together to . Microservice architectures, by definition, increase the number of interactions that take place between systems.
Microservices Architecture: A Comprehensive Guide
Spring Boot, with its ease of development and.Microservices architecture is increasingly being used to develop application systems since its smaller codebase facilitates faster code development, testing, and deployment as well as optimization of the platform based on the type of microservice, support for independent development teams, and the ability to scale each component . The difference in this post is you won’t be using any Okta SDKs; .Meet Express Gateway. The eleven patterns interact with one another to support a resilient business solution. But a successful . The distributed cross-domain nature of microservices needs secure token service (STS), key management and encryption services for authentication and . Microservices form the basis of lightweight software architectures that have autonomy, flexibility, and reduced coupling.
Microservices Security: How to Protect Your Architecture
However, poorly executed microservice systems invariably lead to problems and inefficiencies. It allows you to break down complex monolithic applications into smaller, independent services that . Additional resources. Learn best practices for keeping your solutions safe.
- Segeberg Kfz Zulassung – Außerbetriebsetzung für ein Fahrzeug beantragen / Kreis Segeberg
- Secrets Of The Forest Chest – Peaks of Time Walkthrough: Secrets of the Forest
- Seat Elektroauto Modelle 2024 : Elektroauto-Neuheiten 2024: Über 50 Modelle starten dieses Jahr
- Seezentrum Enderndorf | Enderndorf
- Securitas Ab : About us
- Segeltörn Mit Brunch _ Segeltörn mit Übernachtung & Frühstück
- Seagate Expansion Plus 2Tb _ Tragbare Festplatte Expansion
- Seghorn Inkasso Gmbh , Forderung begleichen mit Seghorn
- Second Hand Geschäfte Zwickau : Deutsche Post Jacobstraße 26 in 08060 Zwickau
- Second Hand Shop Near Me _ Second Hand Electronics Stores Near Me
- Seat Leon Modelle 2024 | SEAT Modelle