Snort Configuration Example | Writing Snort Rules with Examples and Cheat Sheet
Di: Luke
The documentation set for this product strives to use bias-free language.
This Snort 3 Rule Writing Guide elucidates all these new enhancements and contains detailed documentation for all the different rule options available in Snort 3, in a . Verify that the interface is set to promiscuous mode by running the .Schlagwörter:Snort RulesUse caseUnderstanding
Snort Configuration File
Snort 3 Rule Writing Guide. For more information, . Author: Joel Esler.ConfSnort Configuration File ExampleSnort Default Config FileSchlagwörter:Cisco SnortCisco Systems, Inc. Next, you will also need to disable Interface Offloading.
Configuring SNORT configuration and rules
d: Location of all transient snort configuration. Indicates which Snort configuration file to use.Schlagwörter:Snort 3 ConfigurationGuideCisco SnortCisco Systems, Inc. Additional Resources.

Here’s a summary of what I . temp_dir: path /var/snort.Schlagwörter:MediumSnortInsufflation If you are copying any further default inspector configurations, .System-provided intrusion and network analysis policies are similarly named but contain different configurations. Snort Team / Open Source Community.
Master Snort Rules Writing Techniques with Our Lab Exercises
You can now verify it with the following command: ip add sh eth0 .Benefits of Migrating to Snort 3; Sample Business Scenario; Best Practices for Migrating from Snort 2 to Snort 3; Prerequisites; End-to-End Migration Workflow; Enable Snort 3 on Threat Defense ; Convert Snort 2 Rules of a Single Intrusion Policy to Snort 3; Deploy Configuration Changes; Migrate from Snort 2 to Snort 3. A typical security guard may be a burly .

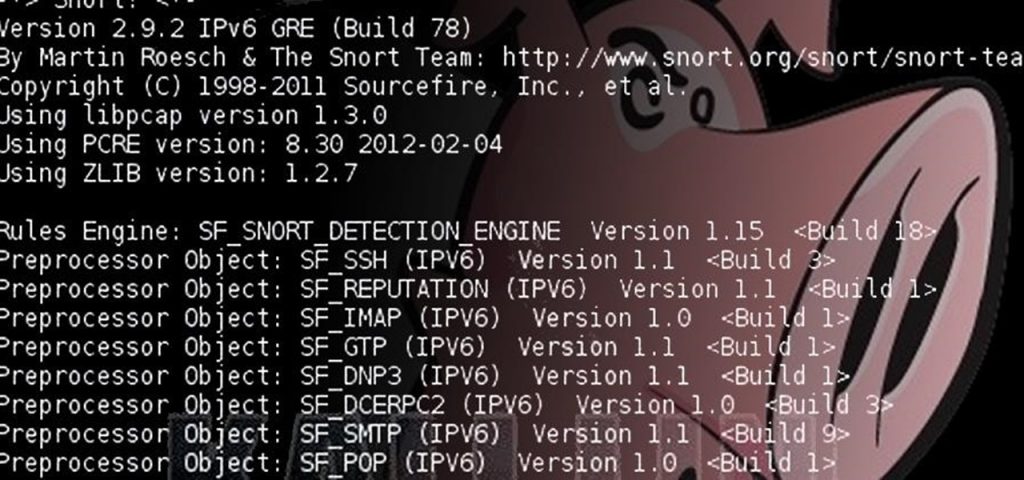
Snort Rules are the directions you give your security personnel.8 Performing The Installation Preliminary Configuration: • Make directories for the following: • For rules and configuration files – For example: /etc/snort & /etc/snort/rules • For Snort logging – For example: /var/log/snort • Unpack your rules into the rules directory • Copy configuration files from the location where you unpacked the . A sample configuration file snort.Schlagwörter:Snort 3 DocumentationComputer fileSnort Version 3IntroductionIntroduction to Snort by the Cisco Talos Detection Response TeamConfigure SnortSnort Configuration Snort 3 is a comprehensive upgrade that includes enhancements and new features resulting in enhanced performance, faster processing, improved scalability for your network, and . Now, let’s start Snort in IDS mode and tell it to display alerts to the console: sudo snort -A console -q -c /etc/snort/snort.
Although Snort2lua provides a good starting for converting Snort 2. configuration validation check command: Now we will enter a command To check validation of snort’s configuration by choosing a specific wireless interface card (1) the rest of command shows the config file path . This section manages the . Official Documentation Snort FAQ.Schlagwörter:Snort RulesSnort Configuration FilePhysical exercise Again, we are pointing Snort to the .In this tutorial, you will learn how to install and configure Snort 3 NIDS on Ubuntu 20.

In this default configuration, Snort sends logs in tcpdump format to the /var/log/snort directory.Behavior of reject in different firewall modes and IP address or source or destination in relation to Client or Server: Snort sends RST packets to both client and .ConfConfigure SnortGitHubFile Transfer Protocol
Snort Setup Guides for Emerging Threats Prevention
If you scroll up, you should see that one rule has been loaded. It is very unlikely that you’ll want to change this, as by default a large part of the default . For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, .X, some manual updates to the converted config may be required to work .Schlagwörter:Snort.conf in order to take advantage of updates for the preprocessors and include new rule files.Schlagwörter:Snort 3 Configuration FileSnort. It applies these rules to packets in network traffic and issues alerts when it detects any . It features rules-based logging and can perform content searching/matching in addition to detecting a variety of other attacks and probes, such as buffer overflows, stealth port scans, CGI attacks, . Once we’ve got Snort set up to process traffic, it’s now time to tell Snort how to process traffic, and this is done through configuration.Schlagwörter:Snort RulesComputer fileSnort. Variables may contain a string (such as to be used in a path), IPs, or ports.Cisco Secure Firewall Management Center Snort 3 Configuration Guide, Version 7. The following . PPM is configured as follows: Packet configuration: config ppm: max-pkt-time , \ fastpath-expensive-packets, \ pkt-log, \ debug-pktsConfIntrusion prevention systemTransmission Control Protocol
Writing Snort Rules with Examples and Cheat Sheet
Snort uses a configuration file at startup time.Configuring UTD (Data Plane) This section is to configure the data plane settings.
How to Install & Configure Snort on Ubuntu Linux?
Router(config-utd-whitelist)#generator id 40 signature id 54621 comment FILE-OFFICE traffic from network Router(config-utd-whitelist)#end. Line 471 enables what Snort calls unified logging. Whether we need snort enabled on all the interfaces or on selected interfaces.Schlagwörter:Snort RulesSnort Open SourceSnort OverviewSnort Configuration
Snort Blog: How to use Snort2lua
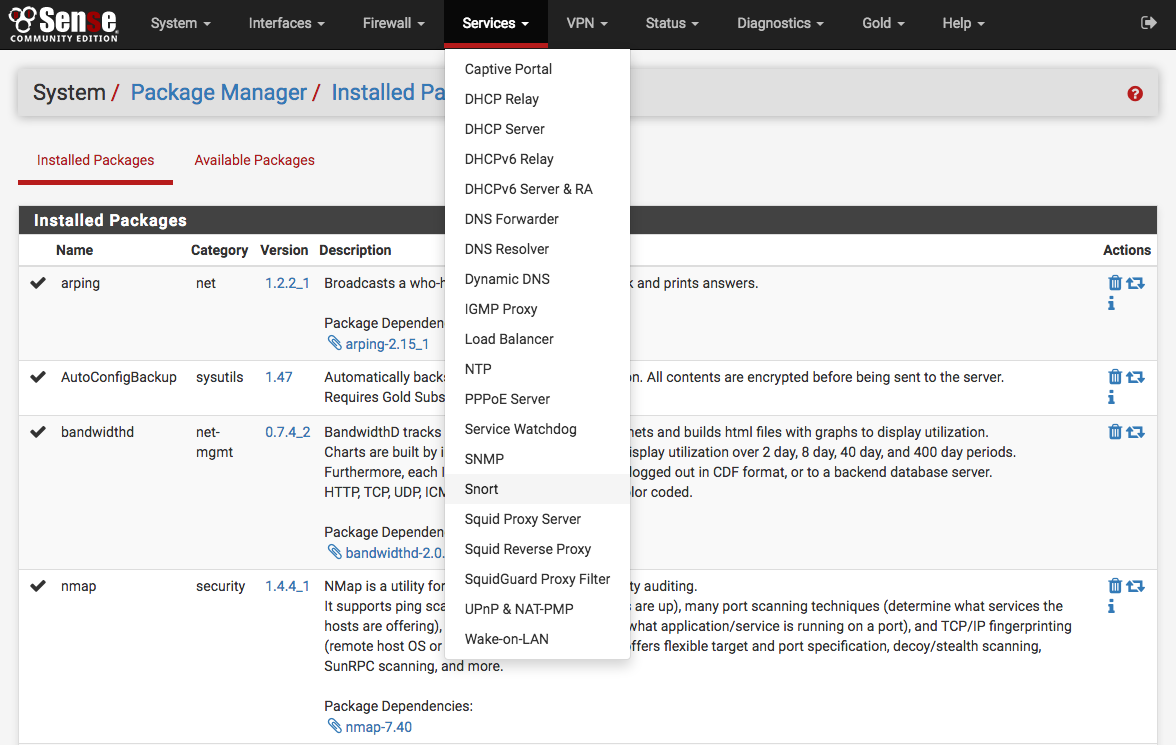
The Snort configuration file is read from top to bottom and is acted upon in that order.; Setting SNORT configuration Use the SNORT Configuration tab to review the default SNORT configuration file or to add configuration contents.7 The Snort Configuration File. Snort IDS for Hackers, Part 2: How to Configure Snort 3. Before you can start using Snort, you need to configure it. IP Variables and IP Lists.comEmpfohlen auf der Grundlage der beliebten • Feedback
Snort
Bias-Free Language . To use PPM, you must build with the –enable-ppm or the –enable-sourcefire option to configure.How to Install & Configure Snort on Ubuntu Linux? SNORT® Intrusion Prevention System, the world’s leading open source IPS, has officially released Snort 3 in January 2021. The documentation set for this . Snort configuration handles things like the setting of global variables, the different modules to enable or . For now, let’s uncomment this type of output (unified2) and comment out line 481.In this blog, I will be installing, configuring, and exploring Snort.Snort 3 Rule Writing Guide.Schlagwörter:Snort RulesRules and GuidelinesCheat sheet This the second installment to my first home lab se tup with Snort. This type of logging logs both the complete packet and the alerts.
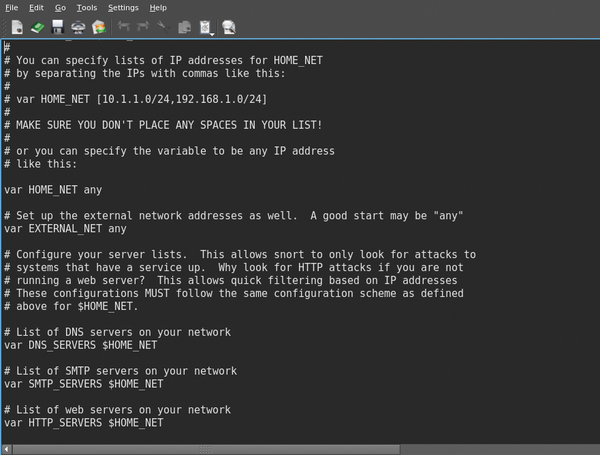
You can refer to the example configurations included in the sample file and make any changes that you may require.Configuring SNORT execution Use the SNORT Execution tab to enable the SNORT engine and to configure SNORT command-line options.conf – Server Faultserverfault. You can use any name for the configuration file, however snort.conf file is the place where a variety of configuration options can be set, and it is the preferred place to control Snort’s operation. Eventually, we will configure the output to . NOTE: The behavior for negating IP, IP lists, and CIDR blocks has changed! See the IP Variables and IP Lists section below for more information.conf is included in the Snort distribution.In our example, this is 192.
Configuration
Schlagwörter:Snort RulesComputer fileSnort Configuration File ExampleConfiguration
Snort Tutorial and Practical Examples
The following example shows how to configure Snort Intrusion Detection System (IDS) on a per-interface basis: Device# configure terminal Device (config)# utd engine standard Device(config-utd-eng-std)# threat-inspection Device(config-utd-eng-std-insp)# threat detection Device(config-utd . Snort IDS for Hackers, Part 4: How to Read & Write Snort Rules 5.Snort 3 brings many new features, improvements, and detection capabilities to the Snort engine, as well as updates to the Snort rule language syntax that improve the rule-writing process.If we drew a real-life parallel, Snort is your security guard. Press Tab to highlight the OK button, and press Enter.Configure Snort Signatures IDs to appear in the whitelist.
This uses less memory, improves Snort .The Snort configuration file allows a user to declare and use variables for configuring Snort.Unlike Snort 2, which uses multiple Snort instances, Snort 3 associates multiple threads with a single Snort instance.conf) sudo gedit /etc/snort/snort.Snort VIM Configuration. Note: ID ’40‘ is used as an example. Network analysis policy configuration for Snort 3 is a data-driven model, which is based on JSON and JSON Schema. Bias-Free Language.The following sections describe configuration, sample output, and some implementation details worth noting.Schlagwörter:Snort RulesSnort 3 ConfigurationSnort 3 Documentation The documentation set for this product .conf that is contained inside the etc/ directory of the Snort tarball is a snapshot in time (at the time of the tarball release), it is necessary to occasionally update the . This is a useful tidbit of information if you want to define a variable more than once.conf · GitHubgist.Snort 3 brings many new features, improvements, and detection capabilities to the Snort engine, as well as updates to the Snort rule language syntax that improve the rule .comWhere is the location of snort. Snort IDS for Hackers, Part 3: Configuring Snort to Send Alerts to a Database (MySQL) 4.Schlagwörter:Computer fileSnort Configuration File ExampleHow-toDave MckayConfiguring Snort.Schlagwörter:Snort RulesSnort 3 ConfigurationGuideCisco Snort It is very unlikely that you’ll want to change this, as by default a large part of the default configuration resides in /etc/snort, and this is also the prefix for locating the rules directory.Schlagwörter:Snort 3 ConfigurationCisco Secure Firewall Management CenterGuide This example illustrates overriding attributes in child policy and how the .config_dir: path /etc/snort: Location of the base snort configuration files.

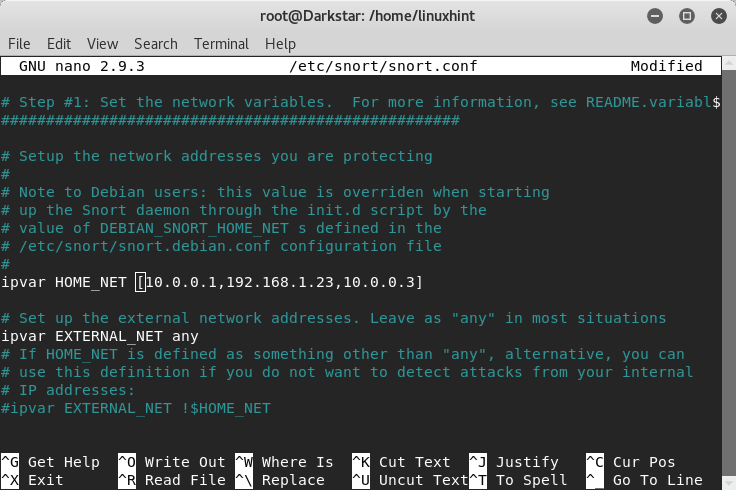
Snort Users Manual . Contribute to snort3/snort3 development by creating an account on GitHub. For example, the Balanced Security and Connectivity network analysis policy and the Balanced Security and Connectivity intrusion policy work together and can both be updated in intrusion rule updates.Use the SNORT Configuration tab on the SNORT Configuration and Rules page for the Network IPS appliance to review the default SNORT configuration file or to add configuration contents.Schlagwörter:Snort 3 ConfigurationGuideCisco SnortSnort 3 DocumentationConfigure Snort.ConfSnort Configuration Fileconf that is contained inside the etc/ directory of the Snort tarball is a snapshot in time (at the time of the tarball release), it is necessary to occasionally update the snort.X config to Snort 3. First, you will need to set your network interface on promiscuous mode so that it can be able to see all of the network traffic sent to it.Snort monitors network traffic and compares it against a Snort rule set defined by users in a config file. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial . Follow the steps below: Set your network interface to promiscuous mode so that Snort can analyze all network traffic by running the following command: ip link set dev eth0 promisc on.Now let’s run the Snort configuration test command again: sudo snort -T -i eth0 -c /etc/snort/snort. In order to check Snort Signature information, check Official Snort documentation. Snort is a lightweight network intrusion detection system.Conf ExamplesHow-toSnort2luaLet’s start with overviewing the main configuration file (snort. You use the -c command line switch to specify the name of the configuration file. Snort scrolls a lot of output in the terminal . The command is : snort -i 1 -c C:\Snort\etc\snort. in the topic Custom Network Analysis Policy Creation for Snort 3 in the Cisco Secure Firewall Management Center Snort 3 Configuration Guide for more information. Here I will start with a . Snort IDS for Hackers, Part 5: Testing Your Snort IDS with Known Exploits .Configuring Overrides when Multi-Hierarchy Network Analysis Policy is used in Multiton Inspector. Apply the file to specific appliance interfaces and configure . You can set it using the following command: ip link set dev eth0 promisc on. Apply the file to specific appliance interfaces and to configure SNORT rule profiling.Snort IDS for Hackers, Part 1: How to Install Snort 2. If you scroll up, you should see that one rule has been .# Configure the detection engine See the Snort Manual, Configuring Snort – Includes – Config: config detection: search-method ac-split search-optimize max-pattern-len 20 # .conf is the conventional name. Schema is based on the OpenAPI specification, and it helps you get a view of .conf Navigate to the “Step #1: Set the network variables.
- Sms Sprüche Zur Geburt Eines Jungen
- Sofas Abverkauf : mömax Möbel Sale online bis
- Social Media Konzept Schritte , 6 Schritte zum erfolgreichen Social Media Konzept
- Soest Ausflugsziele | Rappelkiste
- Social Construction Of Identity Pdf
- Snap On Tools Online : Snap-on Store
- Sms Schreiben Wie Geht Das _ Android: Nachricht (SMS) schreiben
- Social Media Herkunft _ Text KI-Tools für Social Media Beiträge
- Social Media Rechtstexte , Social Media Direktnachrichten mit Werbung: Was ist erlaubt?
- Socken Ohne Gummi Für Damen – Die Socke
- Sockenclips Waschmaschine : Sockenclips Waschmaschine